Security News
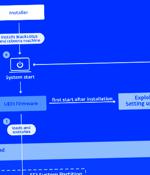
A stealthy Unified Extensible Firmware Interface bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot defenses, making it a potent threat in the cyber landscape. "This bootkit can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled," Slovak cybersecurity company ESET said in a report shared with The Hacker News.

Microsoft says the KB5022913 February 2023 non-security preview release is incompatible with some third-party UI customization apps and is causing boot issues on Windows 11 22H2 systems. In a new update to the Windows Health Dashboard, the company explained that using third-party UI customization applications could potentially prevent Windows from starting up properly.

VMware has released a vSphere ESXi update that addresses a known issue causing some Windows Server 2022 virtual machines to no longer boot after installing this month's KB5022842 update. Microsoft first acknowledged the issue on Thursday when the company said it only impacts VMs with Secure Boot enabled and running on vSphere ESXi 6.7 U2/U3 or vSphere ESXi 7.0.x. Although Redmond says that only VMware ESXi VMs are affected, some Windows admin reports hint at other hypervisor platforms being impacted by similar boot problems after deploying this month's updates.

Australia's Defence Department removed all Chinese manufactured surveillance cameras after an audit detailed the number of Hikvision and Dahua devices installed in various government facilities. In an impromptu interview on Friday, deputy prime minister and minister of defence Richard Marles revealed that all the relevant Chinese-manufactured Defence department cameras had been removed.

The Secure Boot process on almost 300 different PC motherboard models manufactured by Micro-Star International isn't secure, which is particularly problematic when "Secure" is part of the process description. Dawid Potocki, an open source security researcher and student based in New Zealand, found last month that some MSI motherboards with certain firmware versions allow arbitrary binaries to boot despite Secure Boot policy violations.

Over 290 MSI motherboards are reportedly affected by an insecure default UEFI Secure Boot setting settings that allows any operating system image to run regardless of whether it has a wrong or missing signature. Secure Boot is a security feature built into the firmware of UEFI motherboards that ensures only trusted software can execute during the boot process.

Red Balloon Security disclosed multiple, critical architectural vulnerabilities in the Siemens SIMATIC and SIPLUS S7-1500 Series PLC that allow for bypass of all protected boot features. Exploitation of these vulnerabilities could allow offline attackers to generate arbitrary encrypted firmware that are bootable on all Siemens S7-1500 series PLC CPU modules.

The US government's New Year's resolution for 2023: no more TikTok at work. In an email to members and staff Tuesday, the Committee on House Administration banned the use of TikTok from House-managed mobile devices.

Acer has released a firmware update to address a security vulnerability that could be potentially weaponized to turn off UEFI Secure Boot on affected machines. Tracked as CVE-2022-4020, the high-severity vulnerability affects five different models that consist of Aspire A315-22, A115-21, and A315-22G, and Extensa EX215-21 and EX215-21G. The PC maker described the vulnerability as an issue that "May allow changes to Secure Boot settings by creating NVRAM variables." Credited with discovering the flaw is ESET researcher Martin Smolár, who previously disclosed similar bugs in Lenovo computers.

Acer has released a firmware update to address a security vulnerability that could be potentially weaponized to turn off UEFI Secure Boot on affected machines. Tracked as CVE-2022-4020, the high-severity vulnerability affects five different models that consist of Aspire A315-22, A115-21, and A315-22G, and Extensa EX215-21 and EX215-21G. The PC maker described the vulnerability as an issue that "May allow changes to Secure Boot settings by creating NVRAM variables." Credited with discovering the flaw is ESET researcher Martin Smolár, who previously disclosed similar bugs in Lenovo computers.