Security News
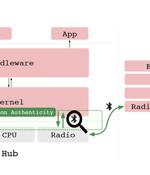
A group of academics has proposed a machine learning approach that uses authentic interactions between devices in Bluetooth networks as a foundation to handle device-to-device authentication reliably. Called "Verification of Interaction Authenticity", the recurring authentication scheme aims to solve the problem of passive, continuous authentication and automatic deauthentication once two devices are paired with one another, which remain authenticated until an explicit deauthentication action is taken, or the authenticated session expires.

Google on Monday announced that it's discontinuing the Bluetooth version of the Titan Security Key and it will only offer devices that have near-field communication functionality. The company will only offer two types of Titan security keys: a USB-A version and a USB-C version, both with NFC capabilities.

Google is discontinuing the Bluetooth Titan Security Key to focus on security keys with Near Field Communication functionality. As part of this move, Google has also announced a new Titan Security Key with USB-C and NFC to go along with the previously available USB-A + NFC security key.

The Zephyr real-time operating system for embedded devices received an update earlier this month that fixes multiple vulnerabilities that can cause a denial-of-service condition and potentially lead to remote code execution. Matias Karhumaa, a senior software engineer at Synopsys, an American electronic design automation company, found eight vulnerabilities in Zephyr after testing the lowest layers of the operating system's Bluetooth LE stack.

Multiple vulnerabilities recently patched in Zephyr's Bluetooth LE stack could be exploited to cause denial of service conditions, prevent further connections, or even leak sensitive information, according to a warning from researchers at the Synopsys Cybersecurity Research Center. The platform includes support for multiple network protocols, including the full Bluetooth LE stack.

Vulnerabilities in the Zephyr real-time operating system's Bluetooth stack have been identified, leaving a wide variety of Internet of Things devices open to attack - unless upgraded to a patched version of the OS. A security advisory released by Synopsys this afternoon highlights eight key vulnerabilities in Zephyr's Bluetooth Low Energy software stack. The vulnerabilities, discovered through use of Synopsys's Defensics fuzzing software, are exploitable when the devices are in advertising mode and accepting connections from remote devices - putting a wide range of gadgets at risk.

Intel has unleashed 29 security advisories to plug up some serious bugs in the BIOS firmware for Intel processors, as well as in its Bluetooth products, Active Management Technology tools, the NUC Mini PC line, and, ironically, in its own security library. "Forty of those, or 55 percent, were found internally through our own proactive security research. Of the remaining 33 CVEs being addressed, 29, or 40 percent, were reported through our bug-bounty program. Overall, 95 percent of the issues being addressed today are the result of our ongoing investments in security assurance, which is consistent with our 2020 Product Security Report."

Intel has pushed out a raft of security advisories for June, bringing its total discovered "Potential vulnerabilities" for the year to date to 132, only a quarter of which were reported by external contributors and the company's bug bounty programme. "Today we released 29 security advisories addressing 73 vulnerabilities," Intel's Jerry Bryant said of the company's latest updates.

Adversaries could exploit newly discovered security weaknesses in Bluetooth Core and Mesh Profile Specifications to masquerade as legitimate devices and carry out man-in-the-middle attacks. "Devices supporting the Bluetooth Core and Mesh Specifications are vulnerable to impersonation attacks and AuthValue disclosure that could allow an attacker to impersonate a legitimate device during pairing," the Carnegie Mellon CERT Coordination Center said in an advisory published Monday.

Researchers working for a French government agency have identified seven new Bluetooth vulnerabilities that could expose many devices to impersonation and other types of attacks. The flaws, discovered by researchers at France's national cybersecurity agency ANSSI, affect devices that support the Bluetooth Core and Mesh specifications, which define technical and policy requirements for devices operating over Bluetooth connections.