Security News
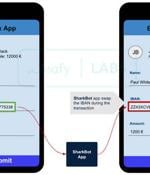
Cybersecurity researchers on Monday took the wraps off a new Android trojan that takes advantage of accessibility features on the devices to siphon credentials from banking and cryptocurrency services in Italy, the U.K., and the U.S. Dubbed "SharkBot" by Cleafy, the malware is designed to strike a total of 27 targets - counting 22 unnamed international banks in Italy and the U.K. as well as five cryptocurrency apps in the U.S. - at least since late October 2021 and is believed to be in its early stages of development, with no overlaps found to that of any known families. "The main goal of SharkBot is to initiate money transfers from the compromised devices via Automatic Transfer Systems technique bypassing multi-factor authentication mechanisms," the researchers said in a report.

Banking malware threats are sharply increasing as cybercriminals target the rising popularity of mobile banking on smartphones, with plots aimed at stealing personal banking credentials and credit card information, a Nokia report reveals. The report, based on data aggregated from network traffic monitored on more than 200 million devices globally, showed an 80%, year-on-year increase in the first half of the year in the number of new banking trojans, which also try to steal SMS messages containing one-time passwords.

A stealthier batch file with at least two layers of obfuscation;. ZIP file, the aforementioned stealthy batch file executes.

A new version of a banking trojan known as Mekotio is being deployed in the wild, with malware analysts reporting that it's using a new, stealthier infection flow. The last notable activity of Mekotio dates back to the summer of 2020 when the trojan's operators deployed it in a campaign targeting Latin American countries.
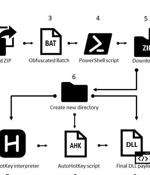
The operators behind the Mekotio banking trojan have resurfaced with a shift in its infection flow so as to stay under the radar and evade security software, while staging nearly 100 attacks over the last three months. The development comes after Spanish law enforcement agencies in July 2021 arrested 16 individuals belonging to a criminal network in connection with operating Mekotio and another banking malware called Grandoreiro as part of a social engineering campaign targeting financial institutions in Europe.
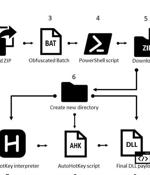
The operators behind the Mekotio banking trojan have resurfaced with a shift in its infection flow so as to stay under the radar and evade security software, while staging nearly 100 attacks over the last three months. The development comes after Spanish law enforcement agencies in July 2021 arrested 16 individuals belonging to a criminal network in connection with operating Mekotio and another banking malware called Grandoreiro as part of a social engineering campaign targeting financial institutions in Europe.

It's easy to forget that the "Obviousness" of many scam emails comes from the fact that the crooks never intended those scams for us in the first place. We received a phish this morning that specifically targeted one of the main South African banks.

The operators behind the BlackRock mobile malware have surfaced back with a new Android banking trojan called ERMAC that targets Poland and has its roots in the infamous Cerberus malware, according to the latest research. "The new trojan already has active distribution campaigns and is targeting 378 banking and wallet apps with overlays," ThreatFabric's CEO Cengiz Han Sahin said in an emailed statement.

A newly spotted banking trojan has been caught leveraging legitimate platforms like YouTube and Pastebin to store its encrypted, remote configuration and commandeer infected Windows systems, making it the latest to join the long list of malware targeting Latin America after Guildma, Javali, Melcoz, Grandoreiro, Mekotio, Casbaneiro, Amavaldo, Vadokrist, and Janeleiro. " interesting new techniques to the pool of Latin American banking trojans' tricks, like using seemingly useless ZIP archives or bundling payloads with decoy BMP images," ESET researchers said in a technical analysis published on Friday.
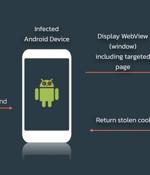
A mix of banking applications, cryptocurrency wallets, and shopping apps from the U.S. and Spain are the target of a newly discovered Android trojan that could enable attackers to siphon personally identifiable information from infected devices, including banking credentials and open the door for on-device fraud. Dubbed S.O.V.A., the current version of the banking malware comes with myriad features to steal credentials and session cookies through web overlay attacks, log keystrokes, hide notifications, and manipulate the clipboard to insert modified cryptocurrency wallet addresses, with future plans to incorporate on-device fraud through VNC, carry out DDoS attacks, deploy ransomware, and even intercept two-factor authentication codes.