Security News

Cybersecurity researchers have discovered a new Android banking malware named MaliBot, which poses as a cryptocurrency mining app or the Chrome web browser to target users in Italy and Spain. MaliBot focuses on stealing financial information such as e-banking service credentials, crypto wallet passwords, and personal details, while it's also capable of snatching two-factor authentication codes from notifications.

A new strain of Android malware has been spotted in the wild targeting online banking and cryptocurrency wallet customers in Spain and Italy, just weeks after a coordinated law enforcement operation dismantled FluBot. The information stealing trojan, codenamed MaliBot by F5 Labs, is as feature-rich as its counterparts, allowing it to steal credentials and cookies, bypass multi-factor authentication codes, and abuse Android's Accessibility Service to monitor the victim's device screen.

10 of the most prolific mobile banking trojans have set their eyes on 639 financial applications that are available on the Google Play Store and have been cumulatively downloaded over 1.01 billion times. These apps alone account for more than 260 million downloads from the official app marketplace.

The ten most prolific Android mobile banking trojans target 639 financial applications that collectively have over one billion downloads on the Google Play Store. Mobile banking trojans hide behind seemingly benign apps like productivity tools and games and commonly sneak into the Google Play Store, Android's official app store.

Despite banks working to improve online security protocols, consumers must also do their part in taking advantage of enhanced security features to keep their accounts safe. Since banks strive to make the digital banking experience as intuitive and frictionless as possible for users, this can also present an opportunity for hackers to access unwitting consumers' bank accounts.

A new social engineering scam is making the rounds, and this one is particularly insidious: It tricks users into sending money to what they think is their own account to reverse a fraudulent charge. The FBI's Internet Crime Complaint Center issued the warning, which it said involves cybercriminals who have definitely done their homework.

A banking trojan for Android that researchers call Fakecalls comes with a powerful capability that enables it to take over calls to a bank's customer support number and connect the victim directly with the cybercriminals operating the malware. While the victim sees the bank's real number on the screen, the connection is to the cybercriminals, who can pose as the bank's customer support representatives and obtain details that would give them access to the victim's funds.

A banking trojan for Android that researchers call Fakecalls comes with a powerful capability that enables it to take over calls to a bank's customer support number and connect the victim directly with the cybercriminals operating the malware. While the victim sees the bank's real number on the screen, the connection is to the cybercriminals, who can pose as the bank's customer support representatives and obtain details that would give them access to the victim's funds.

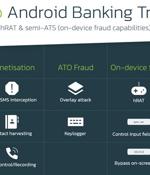
A new Android banking malware named Octo has appeared in the wild, featuring remote access capabilities that allow malicious operators to perform on-device fraud. Octo is an evolved Android malware based on ExoCompact, a malware variant based on the Exo trojan that quit the cybercrime space and had its source code leaked in 2018.
A number of rogue Android apps that have been cumulatively installed from the official Google Play Store more than 50,000 times are being used to target banks and other financial entities. Like other Android banking trojans, the rogue apps are nothing more than droppers, whose primary function is to deploy the malicious payload embedded within them.