Security News
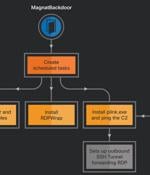
A series of malicious campaigns have been leveraging fake installers of popular apps and games such as Viber, WeChat, NoxPlayer, and Battlefield as a lure to trick users into downloading a new backdoor and an undocumented malicious Google Chrome extension with the goal of stealing credentials and data stored in the compromised systems as well as maintaining persistent remote access. A noteworthy aspect of the intrusions is the use of malvertising as a means to strike individuals who are looking for popular software on search engines to present them links to download fake installers that drop a password stealer called RedLine Stealer, a Chrome extension dubbed "MagnatExtension" that's programmed to record keystrokes and capture screenshots, and an AutoIt-based backdoor that establishes remote access to the machine.

A security researcher has shed light on how invisible characters can be snuck into JavaScript code to introduce security risks, like backdoors, into your software. This week, a researcher has disclosed how certain characters could be injected into JavaScript code to introduce invisible backdoors and security vulnerabilities.

A security researcher has shed light on how invisible characters can be snuck into JavaScript code to introduce security risks, like backdoors, into your software. This week, a researcher has disclosed how certain characters could be injected into JavaScript code to introduce invisible backdoors and security vulnerabilities.

A newly discovered and previously undocumented UEFI bootkit has been used by attackers to backdoor Windows systems by hijacking the Windows Boot Manager since 2012. Bootkits are malicious code planted in the firmware invisible to security software that runs within the operating system since the malware is designed to load before everything else, in the initial stage of the booting sequence.
Cybersecurity researchers on Wednesday disclosed a previously undocumented backdoor likely designed and developed by the Nobelium advanced persistent threat behind last year's SolarWinds supply chain attack, joining the threat actor's ever-expanding arsenal of hacking tools. "While supply-chain attacks were already a documented attack vector leveraged by a number of APT actors, this specific campaign stood out due to the extreme carefulness of the attackers and the high-profile nature of their victims," Kaspersky researchers said.

Kaspersky security researchers have discovered a new backdoor likely developed by the Nobelium hacking group behind last year's SolarWinds supply chain attack. The new malware found by Kaspersky, dubbed Tomiris, was first spotted in June even though the first samples were deployed in the wild in February 2021, one month before the "Sophisticated second-stage backdoor" Sunshuttle was found by FireEye and linked to Nobelium.

Researchers have discovered a campaign delivering a previously unknown backdoor they're calling Tomiris. Namely, Tomiris has a number of similarities to the Sunshuttle second-stage malware that was distributed by Nobelium.

Security intelligence vendor Flashpoint claims to have found forum comments from customers of the REvil ransomware-as-a-service gang, and they're not happy. The gang's malware may contain backdoors that REvil uses to restore encrypted files itself.

Researchers from the Microsoft Threat Intelligence Center have observed the APT it calls Nobelium using a post-exploitation backdoor dubbed FoggyWeb, to attack Active Directory Federation Services servers. Once a server is compromised, the threat group deploys FoggyWeb "To remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificates and token-decryption certificates," he said, which can be used to penetrate into users' cloud accounts.

State-sponsored hackers affiliated with Russia are behind a new series of intrusions using a previously undocumented implant to compromise systems in the U.S., Germany, and Afghanistan. Cisco Talos attributed the attacks to the Turla advanced persistent threat group, coining the malware "TinyTurla" for its limited functionality and efficient coding style that allows it to go undetected.