Security News

Symantec, by Broadcom Software, is tracking the activity under its insect-themed moniker Lancefly, with the attacks making use of a "Powerful" backdoor called Merdoor. "The backdoor is used very selectively, appearing on just a handful of networks and a small number of machines over the years, with its use appearing to be highly targeted," Symantec said in an analysis shared with The Hacker News.

A previously undocumented and mostly undetected variant of a Linux backdoor called BPFDoor has been spotted in the wild, cybersecurity firm Deep Instinct said in a technical report published this week. BPFDoor, first documented by PwC and Elastic Security Labs in May 2022, is a passive Linux backdoor associated with a Chinese threat actor called Red Menshen, which is known to single out telecom providers across the Middle East and Asia since at least 2021.
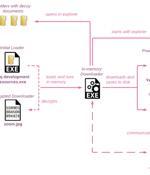
An Iranian nation-state threat actor has been linked to a new wave of phishing attacks targeting Israel that's designed to deploy an updated version of a backdoor called PowerLess. The attack chain documented by Check Point begins with an ISO disk image file that makes use of Iraq-themed lures to drop a custom in-memory downloader that ultimately launches the PowerLess implant.

Threat actors have been observed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor websites as part of an ongoing campaign, Sucuri revealed in a report published last week. The plugin in question is Eval PHP, released by a developer named flashpixx.

Google has addressed a Cloud Platform security vulnerability impacting all users and allowing attackers to backdoor their accounts using malicious OAuth applications installed from the Google Marketplace or third-party providers.Named GhostToken by Astrix Security, the Israeli cybersecurity startup that found and reported it to Google in June 2022, this security flaw was addressed via a global patch that rolled out in early April 2023.

Hackers use a novel method involving RBAC to create persistent backdoor accounts on Kubernetes clusters and hijack their resources for Monero crypto-mining. RBAC is a Kubernetes API access control system allowing admins to define which users or service accounts can access API resources and operations.

Attackers are using Eval PHP, an outdated legitimate WordPress plugin, to compromise websites by injecting stealthy backdoors. Eval PHP is an old WordPress plugin that allows site admins to embed PHP code on pages and posts of WordPress sites and then execute the code when the page is opened in the browser.

A design flaw in Microsoft Azure - that shared key authorization is enabled by default when creating storage accounts - could give attackers full access to your environment, according to Orca Security researchers. "Similar to the abuse of public AWS S3 buckets seen in recent years, attackers can also look for and utilize Azure access keys as a backdoor into an organization," Orca's Roi Nisimi said.
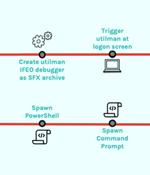
An unknown threat actor used a malicious self-extracting archive file in an attempt to establish persistent backdoor access to a victim's environment, new findings from CrowdStrike show. SFX files are capable of extracting the data contained within them without the need for dedicated software to display the file contents.

A Chinese state-sponsored threat activity group tracked as RedGolf has been attributed to the use of a custom Windows and Linux backdoor called KEYPLUG. "RedGolf is a particularly prolific Chinese state-sponsored threat actor group that has likely been active for many years against a wide range of industries globally," Recorded Future told The Hacker News. The use of KEYPLUG by Chinese threat actors was first disclosed by Google-owned Manidant in March 2022 in attacks targeting multiple U.S. state government networks between May 2021 and February 2022.