Security News

Game developer and publisher Crytek has confirmed that the Egregor ransomware gang breached its network in October 2020, encrypting systems and stealing files containing customers' personal info later leaked on the gang's dark web leak site. "We want to inform you that Crytek was the victim of a ransomware attack by some unknown cyber-criminals," Crytek said in a letter mailed to one of their customers impacted in the incident.

Microsoft has released security updates that block the PetitPotam NTLM relay attack that allows a threat actor to take over a Windows domain. This NTLM relay attack allows the threat actor to take over the domain controller, and thus the Windows domain.

The zero-day attacks against Microsoft's software products continue to pile up with a new warning from Redmond about a zero-day attack hitting a security defect in the Windows Update Medic Service. The Windows Update Medic Service is used to repair Windows Update components from damage so that Windows machines can continue to receive software updates.

Evan Grant, a researcher at network security scanning company Tenable, recently decided to have a go at hacking a home router. Grant's first stop was to download a binay file called httpd, which is the name under which you typically find a home or small business router's web server, used for managing the device from a browser.

Tens of thousands of internet-exposed Microsoft Exchange servers appear to be affected by the ProxyShell vulnerabilities, and they could get compromised at any moment considering that threat actors are already scanning the web for vulnerable devices. ProxyShell is the name given to a series of vulnerabilities - CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207 - that can be chained for unauthenticated remote code execution, allowing an attacker to take complete control of an Exchange server.

Microsoft says that the Azure Sentinel cloud-native SIEM platform is now able to detect potential ransomware activity using the Fusion machine learning model. Microsoft announced today that its cloud-based SIEM now supports Fusion detections for possible ransomware attacks and triggers high severity Multiple alerts possibly related to Ransomware activity detected incidents.

Virtual meetings are vulnerable to a new, exotic attack called Glowworm, which measures an audio output device's LED power light changes and converts them to audio reproductions - allowing cyberattackers to listen to sensitive conversations. As an increasing amount of business is being conducted over platforms like Microsoft Teams, Zoom, Skype and others, the findings present an entirely new attack vector for such electronic communications.

The insurer for Joplin paid $320,00 to an unknown person after a ransomware attack shut down the city's government's computer system last month, Joplin City Manager Nick Edwards said Thursday. The money was paid to keep any sensitive information accessed by the attack from being exposed, Edwards said in a news release.
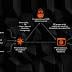
Multiple cybercriminal groups are leveraging a malware-as-a-service solution to distribute a wide range of malicious software distribution campaigns that result in the deployment of payloads such as Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish against individuals in Belgium as well as government agencies, companies, and corporations in the U.S. Dubbed "Prometheus TDS" and available for sale on underground platforms for $250 a month since August 2020, the service is designed to distribute malware-laced Word and Excel documents and divert users to phishing and malicious sites, according to a Group-IB report shared with The Hacker News. More than 3,000 email addresses are said to have been singled out via malicious campaigns in which Prometheus TDS was used to send malicious emails, with banking and finance, retail, energy and mining, cybersecurity, healthcare, IT, and insurance emerging the prominent verticals targeted by the attacks.

The risk of cyberattacks has increased in the last year. The findings come from Trend Micro's biannual Cyber Risk Index report, which measures the gap between respondents' cybersecurity preparedness versus their likelihood of being attacked.