Security News

Ransomware attacks have reached 'stratospheric' levels in Q2 2021, now accounting for 69% of all attacks involving malware. The research also reveals that the volume of attacks on governmental institutions in particular soared from 12% in Q1 2021 to 20% in Q2. And the company's Expert Security Center during the quarter discovered the emergence of B-JDUN, a new RAT used in attacks on energy companies, and Tomiris, new malware that comes with functions for gaining persistence and can send encrypted information about the workstation to an attacker-controlled server.

A high-severity security bug affecting several Netgear small office/home office routers could allow remote code execution via a man-in-the-middle attack. From there, attackers can serve up a malicious database update that triggers RCE, which can be created by downloading and modifying a legitimate Netgear database update, researchers said.

CISA, the Federal Bureau of Investigation, and the National Security Agency warned today of an increased number of Conti ransomware attacks targeting US organizations. The three US federal agencies urge enterprise IT admins to review their organizations' network security posture and implement the immediate actions outlined in the joint advisory to defend against Conti ransomware.

U.S. farmers cooperative NEW Cooperative has suffered a BlackMatter ransomware attack demanding $5.9 million not to leak stolen data and provide a decryptor. NEW Cooperative is a farmer's feed and grain cooperative with over sixty locations throughout Iowa.

Threat actors are targeting voice-over-Internet provider VoIP.ms with a DDoS attack and extorting the company to stop the assault that's severely disrupting the company's operation. On September 16th, 2021, VoIP.ms became the victim of a distributed denial-of-service attack targeting their infrastructure, including DNS name servers.

A spam campaign delivering spear-phishing emails aimed at South American organizations has retooled its techniques to include a wide range of commodity remote access trojans and geolocation filtering to avoid detection, according to new research. Cybersecurity firm Trend Micro attributed the attacks to an advanced persistent threat tracked as APT-C-36, a suspected South America espionage group that has been active since at least 2018 and previously known for setting its sights on Colombian government institutions and corporations spanning financial, petroleum, and manufacturing sectors.

Google on Monday released security updates for Chrome web browser to address a total of 11 security issues, two of which it says are actively exploited zero-days in the wild. Tracked as CVE-2021-30632 and CVE-2021-30633, the vulnerabilities concern an out of bounds write in V8 JavaScript engine and a use after free flaw in Indexed DB API respectively, with the internet giant credited anonymous researchers for reporting the bugs on September 8.

32-year old Matthew Gatrel of St. Charles, Illinois, ran two websites that allowed paying users to launch more than 200,000 DDoS attacks on targets in both the private and public sector. He ran two sites, DownThem and Ampnode, both enabling DDoS attacks.

Add in the fact that Dell found the average organization is managing 10 times more data than they did in 2016 and you have a perfect storm of data security that could threaten to overwhelm organizations and the IT teams that support them. In addition to the aforementioned statistics, Dell also said that 62% of GDPI respondents expressed concern that their existing data protection measures were insufficient to cope with existing malware and ransomware threats.
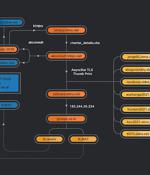
A targeted phishing campaign aimed at the aviation industry for two years may be spearheaded by a threat actor operating out of Nigeria, highlighting how attackers can carry out small-scale cyber offensives for extended periods of time while staying under the radar. Cisco Talos dubbed the malware attacks "Operation Layover," building on previous research from the Microsoft Security Intelligence team in May 2021 that delved into a "Dynamic campaign targeting the aerospace and travel sectors with spear-phishing emails that distribute an actively developed loader, which then delivers RevengeRAT or AsyncRAT.".