Security News

In a concerning development, the notorious Emotet malware now installs Cobalt Strike beacons directly, giving immediate network access to threat actors and making ransomware attacks imminent.Cobalt Strike is very popular among threat actors who use cracked versions as part of their network breaches and is commonly used in ransomware attacks.

A 31-year old Canadian national has been charged in connection to ransomware attacks against organizations in the United States and Canada, a federal indictment unsealed today shows. According to the indictment, between April 2018 through May 2018, Philbert targeted at least ten computers of an organization in the healthcare sector from the District of Alaska.

US universities are being targeted in multiple phishing attacks designed to impersonate college login portals to steal valuable Office 365 credentials. These campaigns are believed to be conducted by multiple threat actors starting in October 2021, with Proofpoint sharing details on the tactics, techniques, and procedures used in the phishing attacks.

The British arm of Dutch supermarket chain Spar has shut hundreds of shops after suffering an "Online attack," the company has confirmed to The Register. "This has not affected all SPAR stores across the North of England," a Spar spokesman told us, "But a number have been impacted over the past 24 hours and we are working to resolve this situation as quickly as possible."
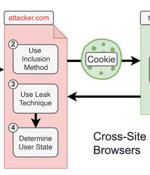
Researchers have discovered 14 new types of cross-site data leakage attacks against a number of modern web browsers, including Tor Browser, Mozilla Firefox, Google Chrome, Microsoft Edge, Apple Safari, Opera, among others. "The purpose of the same-origin policy is to prevent information from being stolen from a trusted website. In the case of XS-Leaks, attackers can nevertheless recognize individual, small details of a website. If these details are tied to personal data, those data can be leaked."

150+ HP multifunction printers open to attackOver 150 HP multifunction printers are open to attack via two exposed physical access port vulnerabilities and two different font parsing vulnerabilities discovered by F-Secure security consultants Timo Hirvonen and Alexander Bolshev. Putting the "Sec" in DevSecOps: An overall reduction of riskIn this Help Net Security interview, Cindy Blake, Senior Security Evangelist at GitLab, talks about the importance of integrating security in DevSecOps and how to overcome the complexity of such integration.

Four different malicious frameworks designed to attack air-gapped networks were detected in the first half of 2020 alone, bringing the total number of such toolkits to 17 and offering adversaries a pathway to cyber espionage and exfiltrate classified information. "All frameworks are designed to perform some form of espionage, [and] all the frameworks used USB drives as the physical transmission medium to transfer data in and out of the targeted air-gapped networks," ESET researchers Alexis Dorais-Joncas and Facundo Muñoz said in a comprehensive study of the frameworks.

A US utility company based in Colorado was hit by a ransomware attack in November that wiped out two decades' worth of records and knocked out billing systems that won't be restored until next week at the earliest. "We are a victim of a malicious cyber security attack. In the middle of an investigation, that is as far as I'm willing to go," DMEA chief exec Alyssa Clemsen Roberts told a public board meeting, as reported by a local paper.

Enterprise software provider Zoho on Friday warned that a newly patched critical flaw in its Desktop Central and Desktop Central MSP is being actively exploited by malicious actors, marking the third security vulnerability in its products to be abused in the wild in a span of four months. The issue, assigned the identifier CVE-2021-44515, is an authentication bypass vulnerability that could permit an adversary to circumvent authentication protections and execute arbitrary code in the Desktop Central MSP server.

IT security researchers from Ruhr-Universität Bochum and the Niederrhein University of Applied Sciences have discovered 14 new types of 'XS-Leak' cross-site leak attacks against modern web browsers, including Google Chrome, Microsoft Edge, Safari, and Mozilla Firefox. These types of side-channel attacks are called 'XS-Leaks,' and allow attacks to bypass the 'same-origin' policy in web browsers so that a malicious website can steal info in the background from a trusted website where the user enters information.