Security News

Taiwanese PC company MSI officially confirmed it was the victim of a cyber attack on its systems. The company said it "Promptly" initiated incident response and recovery measures after detecting "Network anomalies." It also said it alerted law enforcement agencies of the matter.

The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation. That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed DEV-1084.

Following reports of a ransomware attack, Taiwanese PC vendor MSI confirmed today that its network was breached in a cyberattack. In a Friday filing with Taiwan's Stock Exchange, first spotted by PCMag, MSI revealed that some of its information service systems had been affected by a cyberattack reported to the relevant authorities.

The pro-Russia hacker group NoName057(16) reportedly claimed it was behind Denial of Service attacks against the Finnish parliament's website on Tuesday, the day the country joined NATO. The country's Technical Research Centre of Finland was also hacked, according to Finnish news site, YLE. NoName057(16) is the same group that took responsibility for a distributed denial of service attack, taking down the website for the country's parliament last August, and who also attacked Ukraine, the U.S., Poland and other European countries. In a new study, Unveiling the New Threat Landscape, NetScout said that the U.S. national security sector experienced a 16,815% increase in DDoS attacks in the second half of 2022, many related to Killnet.

The Medusa ransomware gang has claimed a cyberattack on the Open University of Cyprus, which caused severe disruptions of the organization's operations. OUC is an online university based in Nicosia, Cyprus, that provides remote learning.

According to Etay Maor, Senior Director Security Strategy at Cato Networks, "It's interesting to note critical infrastructure doesn't necessarily have to be power plants or electricity. A nation's monetary system or even a global monetary system can be and should be considered a critical infrastructure as well." Not to mention the infamous Colonial Pipeline attack, which has become the poster child of critical infrastructure attacks.

Despite the decline in network-detected malware in Q4 2022, endpoint ransomware spiked by 627%, while malware associated with phishing campaigns persisted as a threat, according to WatchGuard. Despite seeing an overall decline in malware, further analysis from WatchGuard Threat Lab researchers looking at Fireboxes that decrypt HTTPS traffic found a higher incidence of malware, indicating malware activity has shifted to encrypted traffic.
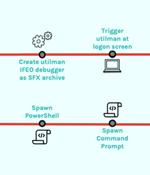
An unknown threat actor used a malicious self-extracting archive file in an attempt to establish persistent backdoor access to a victim's environment, new findings from CrowdStrike show. SFX files are capable of extracting the data contained within them without the need for dedicated software to display the file contents.

The threat actor known as Arid Viper has been observed using refreshed variants of its malware toolkit in its attacks targeting Palestinian entities since September 2022. Also known by the names APT-C-23 and Desert Falcon, the hacking group has been linked to attacks aimed at Palestine and the Middle East at least since 2014.

The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number of cryptocurrency companies. The backdoor's links to North Korea stem from the fact that it "Co-existed on victim machines with AppleJeus, a backdoor attributed to the Korean-speaking threat actor Lazarus," detailing an attack on an unnamed crypto firm located in Southeast Asia in 2020.