Security News

A senior research scientist at Google has devised new CPU attacks to exploit a vulnerability dubbed Downfall that affects multiple Intel microprocessor families and allows stealing passwords, encryption keys, and private data like emails, messages, or banking info from users that share the same computer. Moghimi developed two Downfall attack techniques, Gather Data Sampling - which is also the name Intel uses to refer to the issue and Gather Value Injection - which combines GDS with the Load Value Injection technique disclosed in 2020.

Researchers have discovered a new and powerful transient execution attack called 'Inception' that can leak privileged secrets and data using unprivileged processes on all AMD Zen CPUs, including the latest models. Researchers at ETH Zurich have now combined an older technique named 'Phantom speculation' with a new transient execution attack called 'Training in Transient Execution' to create an even more powerful 'Inception' attack.
In 2022, our in-house research found that 73% of the top attack techniques used in the compromising of critical assets involved mismanaged or stolen credentials - and more than half of the attacks in organizations include some element of Active Directory compromise. So now let's take a look into the anatomy of 3 actual Active Directory attack paths and see how attackers made their way through this environment.

A group of academics has devised a "Deep learning-based acoustic side-channel attack" that can be used to classify laptop keystrokes that are recorded using a nearby phone with 95% accuracy. "When trained on keystrokes recorded using the video conferencing software Zoom, an accuracy of 93% was achieved, a new best for the medium," researchers Joshua Harrison, Ehsan Toreini, and Maryam Mehrnezhad said in a new study published last week.

A team of researchers from British universities has trained a deep learning model that can steal data from keyboard keystrokes recorded using a microphone with an accuracy of 95%. When Zoom was used for training the sound classification algorithm, the prediction accuracy dropped to 93%, which is still dangerously high, and a record for that medium. Such an attack severely affects the target's data security, as it could leak people's passwords, discussions, messages, or other sensitive information to malicious third parties.

PaperCut recently fixed a critical security vulnerability in its NG/MF print management software that allows unauthenticated attackers to gain remote code execution on unpatched Windows servers. While it only impacts servers in non-default configurations where the external device integration setting is toggled, Horizon3 said in a report published on Friday that most Windows PaperCut servers have it enabled.

Serco Inc, the Americas division of multinational outsourcing company Serco Group, has disclosed a data breach after attackers stole the personal information of over 10,000 individuals from a third-party vendor's MoveIT managed file transfer server. "On June 30, 2023, Serco was made aware that our third-party benefits administration provider, CBIZ, experienced a ransomware attack and data breach," the company explained.

Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by malicious actors to deploy web shells, according to the Shadowserver Foundation. The non-profit said the attacks take advantage of CVE-2023-3519, a critical code injection vulnerability that could lead to unauthenticated remote code execution.
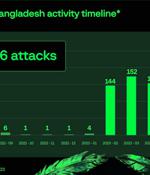
A hacktivist group known as Mysterious Team Bangladesh has been linked to over 750 distributed denial-of-service (DDoS) attacks and 78 website defacements since June 2022. "The group most...

Collide cached data, and measure the power required. If the CPU keeps track of the RAM addresses that you've used recently, and can guess well enough which ones you're likely to use again soon, it can keep them temporarily in its cache memory and thus greatly speed up your second access to those values, and the third access, the fourth, and so on.