Security News
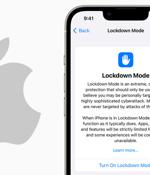
Apple on Wednesday announced it plans to introduce an enhanced security setting called Lockdown Mode in iOS 16, iPadOS 16, and macOS Ventura to safeguard high-risk users against "Highly targeted cyberattacks." Lockdown Mode, when enabled, "Hardens device defenses and strictly limits certain functionalities, sharply reducing the attack surface that potentially could be exploited by highly targeted mercenary spyware," Apple said in a statement.

Apple announced that a new security feature known as Lockdown Mode will roll out with iOS 16, iPadOS 16, and macOS Ventura to protect high-risk individuals like human rights defenders, journalists, and dissidents against targeted spyware attacks. Once enabled, the Lockdown Mode will provide Apple customers with messaging, web browsing, and connectivity protections designed to block mercenary spyware used by government-backed hackers to monitor their Apple devices after infecting them with malware.

One of the commissioners of the U.S. Federal Communications Commission has renewed calls asking for Apple and Google to boot the popular video-sharing platform TikTok from their app stores citing "Its pattern of surreptitious data practices." "It is clear that TikTok poses an unacceptable national security risk due to its extensive data harvesting being combined with Beijing's apparently unchecked access to that sensitive data," Brendan Carr, a Republican member of the FCC, wrote in a letter to Apple and Google's chief executives.

A security flaw in Apple Safari that was exploited in the wild earlier this year was originally fixed in 2013 and reintroduced in December 2016, according to a new report from Google Project Zero. In early February 2022, Apple shipped patches for the bug across Safari, iOS, iPadOS, and macOS, while acknowledging that it "May have been actively exploited."

It leverages "Speculative execution attacks to bypass an important memory protection mechanism, ARM Pointer Authentication, a security feature that is used to enforce pointer integrity," MIT researchers Joseph Ravichandran, Weon Taek Na, Jay Lang, and Mengjia Yan said in a new paper. The vulnerability is rooted in pointer authentication codes, a line of defense introduced in arm64e architecture that aims to detect and secure against unexpected changes to pointers - objects that store a memory address - in memory.

A new hardware attack targeting Pointer Authentication in Apple M1 CPUs with speculative execution enables attackers to gain arbitrary code execution on Mac systems. Discovered by researchers at MIT's Computer Science & Artificial Intelligence Laboratory, this new class of attack would allow threat actors with physical access to Macs with Apple M1 CPUs to access the underlying filesystem.

Apple's M1 chip has been found to contain a hardware vulnerability that can be abused to disable one of its defense mechanisms against memory corruption exploits, giving such attacks a greater chance of success. MIT CSAIL computer scientists on Friday said they have identified a way to bypass the M1 chip's pointer authentication, a security mechanism that tries to prevent an attacker from modifying memory references without being detected.

Apple has introduced a Rapid Security Response feature in iOS 16 and macOS Ventura that's designed to deploy security fixes without the need for a full operating system version update. "MacOS security gets even stronger with new tools that make the Mac more resistant to attack, including Rapid Security Response that works in between normal updates to easily keep security up to date without a reboot," the company said in a statement on Monday.

At WWDC 2022, Apple has announced and previewed iOS 16 and iPad OS 16, macOS 13, watchOS 9, their new M2 chips, new MacBook Air and Pro, as well as new tools, technologies, and APIs for developers focusing on Apple's platforms. Apple extends passwordless authentication with passkeys.

Apple touts Passkey, its new privacy feature, at WWDC 2022. During its WWDC, Apple introduced the next version of macOS, codenamed Ventura, which includes a new privacy feature called Passkey, a digital key designed to help protect users from hackers by completely replacing a user's passwords.