Security News

Cybersecurity researchers have documented a novel post-exploit persistence technique on iOS 16 that could be abused to fly under the radar and main access to an Apple device even when the victim believes it is offline. The method "Tricks the victim into thinking their device's Airplane Mode works when in reality the attacker has planted an artificial Airplane Mode which edits the UI to display Airplane Mode icon and cuts internet connection to all apps except the attacker application," Jamf Threat Labs researchers Hu Ke and Nir Avraham said in a report shared with The Hacker News.

As device diversification continues and more Apple devices enter corporate environments, IT leaders face added management complexity. This new device management standard is built around the concept of shifting device management from centralized servers onto the devices themselves.

Sophos released new findings on CryptoRom scams—a subset of pig butchering schemes designed to trick users of dating apps into making fake cryptocurrency investments. Since May, Sophos X-Ops has...

Turns out, Apple's App Store can't accept the new name for Twitter's iOS app because of minimum character requirements. This week, both Google Play and Apple's App Store pushed updated versions of the Twitter app respectively for Android and iOS users.

Apple has announced plans to require developers to submit reasons to use certain APIs in their apps starting later this year with the release of iOS 17, iPadOS 17, macOS Sonoma, tvOS 17, and watchOS 10 to prevent their abuse for data collection. The iPhone maker said it's making the move to ensure that such APIs are not abused by app developers to collect device signals to carry out fingerprinting, which could be employed to uniquely identify users across different apps and websites for other purposes such as targeted advertising.

According to the company, this change to the App Store API rules ensures developers don't abuse APIs for user fingerprinting. Developers must choose one or more approved reasons that accurately align with their app's API usage.
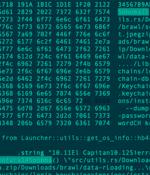
A new malware family called Realst has become the latest to target Apple macOS systems, with a third of the samples already designed to infect macOS 14 Sonoma, the upcoming major release of the operating system. Written in the Rust programming language, the malware is distributed in the form of bogus blockchain games and is capable of "Emptying crypto wallets and stealing stored password and browser data" from both Windows and macOS machines.

Apple has released fixes for several security flaws that affect its iPhones, iPads, macOS computers, and Apple TV and watches, and warned that some of these bugs have already been exploited. Apple credits Kaspersky researchers Valentin Pashkov, Mikhail Vinogradov, Georgy Kucherin, Leonid Bezvershenko, and Boris Larin with finding this bug, which looks similar to the kernel vulnerability used to infect iPhones with TriangleDB spyware and also uncovered by the aforementioned team.

Two weeks ago, we urged Apple users with recent hardware to grab the company's second-ever Rapid Response patch. CVE-2023-37450: an anonymous researcher The next-best thing to zero-click attacks Technically, code execution bugs that can be triggered by getting you to look at a web page that contains booby-trapped content don't count as so-called zero-click attacks.

Apple has patched an exploited zero-day kernel vulnerability in iOS, iPadOS, macOS, watchOS and tvOS. CVE-2023-38606 fix has been backported. In early July, Apple fixed an actively exploited zero-day vulnerability in WebKit.