Security News

Apple made a big change in November 2017 when it released the iPhone X: It ditched Touch ID fingerprint security for a new face-based biometric sign-on tool called Face ID. The fingerprint scanner on most post-iPhone X Apple products is gone, and in its place is a new camera array capable of capturing a face map that is, according to Apple, 20 times less likely to be hacked than a Touch ID fingerprint. Face ID maps faces in a similar way to how Touch ID maps fingerprints: It doesn't store an image, but instead makes a map of the face using data points.

Surprises often arise when connecting two iPhones to the same Apple ID. Addressing several key settings helps avoid common mistakes. Although connecting two iPhones to the same Apple ID has its advantages - including expanding your or a partner's access to your documents, spreadsheets and presentations - unpleasant surprises can arise such as unintentionally revealing contact and calendar information and mistakenly sending texts from the wrong number.
The three zero-day flaws addressed by Apple on September 21, 2023, were leveraged as part of an iPhone exploit chain in an attempt to deliver a spyware strain called Predator targeting former...

Apple has emitted patches this week to close security holes that have been exploited in the wild by commercial spyware. We've just learned today that the Predator spyware sold by Intellexa used these vulnerabilities to infect at least one target's iPhone.

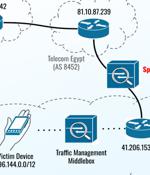
Security researchers with The Citizen Lab and Google's Threat Analysis Group revealed today that three zero-days patched by Apple on Thursday were abused as part of an exploit chain to install Cytrox's Predator spyware. Google TAG also observed the attackers using a separate exploit chain to drop Predator spyware on Android devices in Egypt, exploiting CVE-2023-4762-a Chrome bug patched on September 5th-as a zero-day to gain remote code execution.

Apple has released updates for iOS and iPadOS, macOS, watchOS, and Safari to fix three zero-day vulnerabilities exploited "Against versions of iOS before iOS 16.7.". Earlier this month, Apple closed two zero-day vulnerabilities that have been chained together by attackers to deliver NSO Group's Pegasus spyware.

Apple has released yet another round of security patches to address three actively exploited zero-day flaws impacting iOS, iPadOS, macOS, watchOS, and Safari, taking the total tally of zero-day...

Apple released emergency security updates to patch three new zero-day vulnerabilities exploited in attacks targeting iPhone and Mac users, for a total of 16 zero-days fixed this year.While Apple has yet to provide additional details regarding the flaws' exploitation in the wild, Citizen Lab and Google Threat Analysis Group security researchers have often disclosed zero-day bugs abused in targeted spyware attacks targeting high-risk individuals, including journalists, opposition politicians, and dissidents.

The Agence Nationale des Fréquences has asked Apple to withdraw iPhone 12 smartphones from the French market because the device emits radiofrequency energy that is beyond the limit permitted to be absorbed by the human body. ANFR says it recently conducted measurements on 141 phones available on the French market by contracting an accredited laboratory, where it found that iPhone 12's SAR value for limbs is 5.74 W/kg, exceeding the 4.0 W/kg limit by 43.5%. As such, the agency demands that Apple withdraws all iPhone 12 devices from the French market and takes the required action to make them compliant with European regulations.

Apple released security updates for older iPhones to fix a zero-day vulnerability tracked as CVE-2023-41064 that was actively exploited to infect iOS devices with NSO's Pegasus spyware. Apple released fixes for the two flaws with macOS Ventura 13.5.2, iOS 16.6.1, iPadOS 16.6.1, and watchOS 9.6.2, and CISA published an alert requiring federal agencies to patch by October 2, 2023.