Security News

The Roaming Mantis SMS phishing campaign has finally reached Europe, as researchers detect campaigns targeting Android and iPhone users in Germany and France with malicious apps and phishing pages. Roaming Mantis is a credential theft and malware distribution campaign that uses SMS phishing to distribute malicious Android apps as standalone APK files outside the Google Play Store.
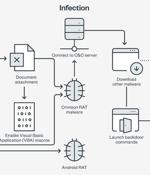
A politically motivated advanced persistent threat group has expanded its malware arsenal to include a new remote access trojan in its espionage attacks aimed at Indian military and diplomatic entities. Called CapraRAT by Trend Micro, the implant is an Android RAT that exhibits a high "Degree of crossover" with another Windows malware known as CrimsonRAT that's associated with Earth Karkaddan, a threat actor that's also tracked under the monikers APT36, Operation C-Major, PROJECTM, Mythic Leopard, and Transparent Tribe.

Microsoft says threat and vulnerability management support for Android and iOS has reached general availability in Microsoft Defender for Endpoint, the company's enterprise endpoint security platform."Threat and vulnerability management in Microsoft Defender for Endpoint continuously monitors and identifies impacted devices, assesses associated risks in the environment, and provides intelligent prioritization and integrated workflows to seamlessly remediate vulnerabilities."

Another Android trojan called TeaBot has been observed lurking on the Google Play Store in the form of an app named "QR Code Reader - Scanner App," attracting no fewer than 100,000 downloads while delivering 17 different variants of the malware between December 6, 2021, and January 17, 2022. BitDefender said it identified four more dropper apps - 2FA Authenticator, QR Scanner APK, QR Code Scan, and Smart Cleaner - that were available on the Play Store and distributed the TeaBot malware since at least April 2021.

Called 'Dark Herring', the operation used 470 Google Play Store apps and affected over 100 million users worldwide, potentially causing hundreds of millions of USD in total losses. In total, the fraudulent apps were installed by 105 million users in 70 countries, subscribing them to premium services that charged $15 per month through Direct Carrier Billing.

If your Android phone initiates a factory reset out of the blue, there's a chance it has been infected with the BRATA banking malware and you've just been ripped off. Through the years, BRATA evolved primarily into banking malware and has lately been aimed against Android users in Europe and the rest of Latin America.

Nearly 500 malicious apps lurking on the Google Play Store have successfully installed Dark Herring malware - a cash-stealer intended to add sneaky charges onto mobile carrier bills - on more than 100 million Android devices across the globe. Dark Herring malware was discovered by a research team with Zimperium, who estimate the amount the campaign has been able to steal totals in the hundreds of millions, in increments of $15 a month per victim.
Microsoft announced today that they would be releasing new Windows 11 features next month, including a preview of the long-awaited Android Apps on Windows 11 feature, a new windows sharing feature, taskbar improvements, and redesigned Notepad and Media Player apps. "Next month we're bringing new experiences to Windows that include a public preview of how you can use Android apps on Windows 11 through the Microsoft Store and our partnerships with Amazon and Intel, taskbar improvements with call mute and unmute, easier window sharing and bringing weather to the taskbar, plus the introduction of two new redesigned apps, Notepad and Media Player," Panay shared in a new blog post.

New FluBot and TeaBot malware distribution campaigns have been spotted, using typical smishing lures or laced apps against Android users in Australia, Germany, Poland, Spain, and Romania. TeaBot is a different Android banking trojan discovered in January 2021 and has a global reach.

Researchers have discovered a raft of active campaigns delivering the Flubot and Teabot trojans through a variety of delivery methods, with threat actors using smishing and malicious Google Play apps to target victims with fly-by attacks in various regions across the globe. Researchers from Bitdefender Labs said they have intercepted more than 100,000 malicious SMS messages trying to distribute Flubot malware since the beginning of December, according to a report published Wednesday.