Security News

SharkBot banking malware has infiltrated the Google Play Store, the official Android app repository, posing as an antivirus with system cleaning capabilities. SharkBot was discovered in Google Play by researchers at the NCC Group, who today published a detailed technical analysis of the malware.
An Apple AirTag is a Bluetooth-based device finder released in April 2021 that allows owners to track the device using Apple's 'Find My' service. Although Apple has implemented an intricate anti-stalking system to prevent cases of abuse, stealthy AirTag tracking continues to remain a problem.

An Apple AirTag is a Bluetooth-based device finder released in April 2021 that allows owners to track the device using Apple's 'Find My' service. The university researchers decided to do something about the Apple AirTag privacy problem in the Android world and reverse-engineered the iOS tracking detection to understand its inner workings better.

A security analyst has devised a way to capture Visual Voice Mail credentials on Android devices and then remotely listen to voicemail messages without the victim's knowledge. Visual Voice Mail is a voicemail system used by numerous mobile carriers that allow customers to view, listen to, and manage voicemails in any order.

New Xenomorph Android malware targets more than 50 banking and financial applications. Figure B. The Alien malware has more overall capabilities than Xenomorph, which is far more targeted at stealing banking information.
An analysis of SMS phone-verified account services has led to the discovery of a rogue platform built atop a botnet involving thousands of infected Android phones, once again underscoring the flaws with relying on SMS for account validation. SMS PVA services, since gain prevalence in 2018, provide users with alternative mobile numbers that can be used to register for other online services and platforms, and help bypass SMS-based authentication and single sign-on mechanisms put in place to verify new accounts.
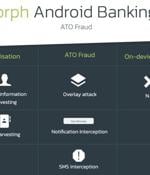
A new Android banking trojan with over 50,000 installations has been observed distributed via the official Google Play Store with the goal of targeting 56 European banks and carrying out harvesting sensitive information from compromised devices. Xenomorph, like Alien and ERMAC, is yet another example of an Android banking trojan that's focused on circumventing Google Play Store's security protections by masquerading as productivity apps such as "Fast Cleaner" to trick unaware victims into installing the malware.

A new malware called Xenomorph distributed through Google Play Store has infected more than 50,000 Android devices to steal banking information. Researchers at fraud and cybercrime prevention company ThreatFabric analyzing Xenomorph found code that is similar to Alien banking trojan.

Google on Wednesday announced plans to bring its Privacy Sandbox initiatives to Android in a bid to expand its privacy-focused, but also less disruptive, advertising technology beyond the desktop web. "The Privacy Sandbox on Android builds on our existing efforts on the web, providing a clear path forward to improve user privacy without putting access to free content and services at risk," Anthony Chavez, vice president of product management for Android security and privacy, said.

Google plans to extend its rework of web ad technology - the optimistically named Privacy Sandbox - to Android devices in an effort to limit the misuse of data in its mobile ecosystem. It began to take shape a year after Google undertook Project Strobe, a rethink of Google Account and Android data access in the wake of ongoing security and privacy problems.