Security News

Several adware apps promoted aggressively on Facebook as system cleaners and optimizers for Android devices are counting millions of installations on Google Play store. To evade deletion, the apps hide on the victim's device by constantly changing icons and names, masquerading as Settings or the Play Store itself.
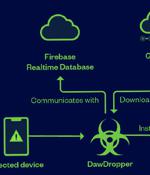
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware. These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others.

As many as 30 malicious Android apps with cumulative downloads of nearly 10 million have been found on the Google Play Store distributing adware. While masquerading as innocuous apps, their primary goal is to request permissions to show windows over other apps and run in the background in order to serve intrusive ads.

A new batch of malicious Android apps filled with adware and malware was found on the Google Play Store that have been installed close to 10 million times on mobile devices. If you installed any of these apps before their removal from the Play Store, you will still need to uninstall them from your device manually and run an AV scan to clean any remnants.

The mobile threat campaign tracked as Roaming Mantis has been linked to a new wave of compromises directed against French mobile phone users, months after it expanded its targeting to include European countries. Attack chains involving Roaming Mantis, a financially motivated Chinese threat actor, are known to either deploy a piece of banking trojan named MoqHao or redirect iPhone users to credential harvesting landing pages that mimic the iCloud login page.

Google on Thursday said it's backtracking on a recent change that removed the app permissions list from the Google Play Store for Android across both the mobile app and the web. "We heard your feedback that you find the app permissions section in Google Play useful, and we've decided to reinstate it. The app permissions section will be back shortly."
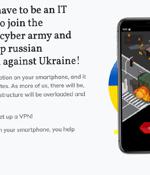
Russian threat actors capitalized on the ongoing conflict against Ukraine to distribute Android malware camouflaged as an app for pro-Ukrainian hacktivists to launch distributed denial-of-service attacks against Russian sites. "The apps were not distributed through the Google Play Store, but hosted on a domain controlled by the actor and disseminated via links on third party messaging services."

Google on Tuesday officially announced support for DNS-over-HTTP/3 for Android devices as part of a Google Play system update designed to keep DNS queries private. To that end, Android smartphones running Android 11 and higher are expected to use DoH3 instead of DNS-over-TLS, which was incorporated into the mobile operating system with Android 9.0.

Google has added support for the DNS-over-HTTP/3 protocol on Android 11 and later to increase the privacy of DNS queries while providing better performance. Roid previously supported DNS-over-TLS for version 9 and later to bolster DNS query privacy, but this system inevitably slowed down DNS requests due to the encryption overhead. Moreover, DoT requires a complete renegotiation of the new connection when changing networks.

Kremlin-backed criminals are trying to trick people into downloading Android malware by spoofing a Ukrainian military group, according to Google security researchers. The CyberAzov app promises to "Help stop Russian aggression against Ukraine" by deploying Denial of Service attacks against set Russian targets, according to the phony website.