Security News

Threat hunters have identified a new variant of Android malware called MoqHao that automatically executes on infected devices without requiring any user interaction. "Typical MoqHao requires users...

A new version of the XLoader Android malware was discovered that automatically executes on devices it infects, requiring no user interaction to launch. XLoader, aka MoqHao, is an Android malware operated and likely created by a financially motivated threat actor named 'Roaming Mantis,' previously seen targeting users in the U.S., U.K., Germany, France, Japan, South Korea, and Taiwan.
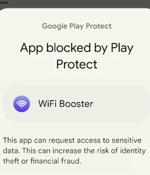
Google has unveiled a new pilot program in Singapore that aims to prevent users from sideloading certain apps that abuse Android app permissions to read one-time passwords and gather sensitive...

Google has launched a new pilot program to fight financial fraud by blocking the sideloading of Android APK files that request access to risky permissions. These files are commonly distributed through third-party sites, allowing you to install apps outside of Google Play.
The threat actor known as Patchwork likely used romance scam lures to trap victims in Pakistan and India, and infect their Android devices with a remote access trojan called VajraSpy. Slovak...

An Android remote access trojan known as VajraSpy was found in 12 malicious applications, six of which were available on Google Play from April 1, 2021, through September 10, 2023. The malicious apps, which have now been removed from Google Play but remain available on third-party app stores, are disguised as messaging or news apps.

A proof-of-concept exploit for a local privilege elevation flaw impacting at least seven Android original equipment manufacturers is now publicly available on GitHub. Tracked as CVE-2023-45779, the flaw was discovered by Meta's Red Team X in early September 2023 and was addressed in Android's December 2023 security update without disclosing details an attacker could use to discern and exploit it.

Several public and popular libraries abandoned but still used in Java and Android applications have been found susceptible to a new software supply chain attack method called MavenGate. "Access to...

Microsoft plans to provide Windows 11 users with almost instant access to photos and screenshots they've taken on their Android smartphones. The new feature "Introduces the ability to effortlessly access and edit your most recent photos and screenshots from your Android mobile device in Snipping Tool on your PC," the Windows Insider team said.

A previously unknown cybercrime syndicate named 'Bigpanzi' has been making significant money by infecting Android TV and eCos set-top boxes worldwide since at least 2015. Bigpanzi infects the devices via firmware updates or backdoored apps the users are tricked into installing themselves, as highlighted in a September 2023 report by Dr. Web.