Security News > 2024 > May

Alexey Pertsev, one of the main developers of the Tornado Cash cryptocurrency tumbler has been sentenced to 64 months in prison for his part in helping launder more than $2 billion worth of...

An unnamed European Ministry of Foreign Affairs (MFA) and its three diplomatic missions in the Middle East were targeted by two previously undocumented backdoors tracked as LunarWeb and LunarMail....

Here’s How to Enhance Your Cyber Resilience with CVSS In late 2023, the Common Vulnerability Scoring System (CVSS) v4.0 was unveiled, succeeding the eight-year-old CVSS v3.0, with the aim...

Trying to configure or set up a VPN on your Android? Learn how to get started with our step-by-step guide.
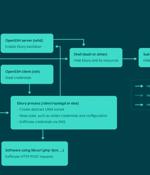
A malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from...

While cloud adoption has been top of mind for many IT professionals for nearly a decade, it’s only in recent months, with industry changes and announcements from key players, that many recognize...

A Dutch court on Tuesday sentenced one of the co-founders of the now-sanctioned Tornado Cash cryptocurrency mixer service to 5 years and 4 months in prison. While the name of the...

Microsoft has addressed a total of 61 new security flaws in its software as part of its Patch Tuesday updates for May 2024, including two zero-days which have been actively exploited in the wild....

A more sustainable, effective, and proactive approach to data privacy compliance is privacy by design. Supporting data enablement across the organization, while providing controls for them to govern data use across the data estate, will help to unlock the value of data.

As a Cybersecurity Analyst, you will be responsible for monitoring and analyzing security events using company's Security Information and Event Management platform and recommending actions to mitigate potential threats. As a Cyber Security Specialist, you will be responsible for developing and implementing strategic cybersecurity initiatives, ensuring the confidentiality, integrity, and availability of company's information assets.