Security News > 2024 > April

Synlab Italia has suspended all its medical diagnostic and testing services after a ransomware attack forced its IT systems to be taken offline.Part of the Synlab group that is present in 30 countries worldwide, the Synlab Italia network operates 380 labs and medical centers across Italy.

The attacker is exploiting a property of GitHub: comments to a particular repo can contain files, and those files will be associated with the project in the URL. What this means is that someone can upload malware and "Attach" it to a legitimate and trusted project. As the file's URL contains the name of the repository the comment was created in, and as almost every software company uses GitHub, this flaw can allow threat actors to develop extraordinarily crafty and trustworthy lures.
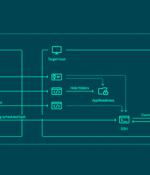
The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data. Russian cybersecurity firm Kaspersky...

BleepingComputer recently reported how a GitHub flaw, or possibly a design decision, is being abused by threat actors to distribute malware using URLs associated with Microsoft repositories, making the files appear trustworthy. While most of the malware-associated activity was based around the Microsoft GitHub URLs, this "Flaw" could be abused with any public repository on GitHub or GitLab, allowing threat actors to create very convincing lures.

With numerous VPN options available for iPhone users, choosing the right app can be a challenge. To help simplify the selection process, we have curated a list of the best VPNs for iPhone users.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Russian hacker group Sandworm aimed to disrupt operations at around 20 critical infrastructure facilities in Ukraine, according to a report from the Ukrainian Computer Emergency Response Team. The attacks occurred in March and in some cases the hackers were able to infiltrate the targeted network by poisoning the supply chain to deliver compromised or vulnerable software, or through the software provider's ability to access organization's systems for maintainance and technical suport.

MITRE has been breached by attackers via two zero-day vulnerabilities in Ivanti's Connect Secure VPN devices. The attackers have also managed to move laterally and compromise the company network's VMware infrastructure, MITRE confirmed late last week.

Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised by a cyberattack. Yes, over half. And this, in a world where enterprises...