Security News > 2024 > March
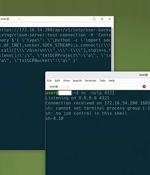
The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber threat actors exploiting known security flaws in Ivanti Connect Secure and Ivanti Policy Secure...

In this Help Net Security interview, Geoffrey Mattson, CEO of Xage Security, discusses the evolution of the Joint Cyber Defense Collaborative since its 2021 inception and tackles its 2024 strategic priorities in response to escalating cyber threats. For 2024, the prevailing theme across its current priorities is cyber hardening and bracing for impact.

Eficode research indicates that 96% of developers use AI tools, with most coders bypassing security policies to use them. With no standardized AI tool regulations, researchers advocate for stronger governance frameworks and AI security policies in organizations' DevOps strategies to encompass the challenges and opportunities AI presents.
GitHub on Thursday announced that it’s enabling secret scanning push protection by default for all pushes to public repositories. “This means that when a supported secret is detected in any push...

NTT West president Masaaki Moribayashi announced his resignation on Thursday, effective at the end of March, in atonement for the leak of data pertaining to 9.28 million customers that came to light last October. Often resignations are avoided if a leader simply offers up a chunk of their salary instead. On Thursday, NTT West apologized for the leak and released details of a related investigation.

81% of respondents say the new SEC cybersecurity disclosure ruling will substantially impact their business. The SEC's new cybersecurity rules on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure took effect on Dec. 15, 2023.

75% of external business-to-business relationships that enabled third-party breaches involved software or other technology products and services. The remaining 25% of third-party breaches involved non-technical products or services.

A malware distribution campaign that began last May with a handful of malicious software packages uploaded to the Python Package Index has spread to GitHub and expanded to reach at least 100,000 compromised repositories. According to security firm Apiiro, the campaign to poison code involves cloning legitimate repos, infecting them with malware loaders, uploading the altered files to GitHub under the same name, then forking the poisoned repo thousands of times and promoting the compromised code in forums and on social media channels.

Dashlane is one of few password managers that offers a completely free version. While limited in comparison to Dashlane Premium, the free version still allows users access to key password management features.