Security News > 2023 > October

The success of cyber attacks in Australia could make an "Assume-breach" approach to cyber security inevitable and cause IT teams to shift their focus to protecting data backups at all costs. Rubrik's technology leader for Australia and New Zealand, Dale Heath, has said many local organizations still have an operational resilience mindset and are relying on systems not designed for cyber resilience when ransomware attackers breach perimeter defenses.

Partner Content According to the Cyber Security Breaches Survey 26 percent of medium businesses, 37 percent of large businesses and 25 percent of high-income charities have experienced cyber crime in the last 12 months. With cyber security experts in high demand, finding the right talent to help protect your business can be difficult.
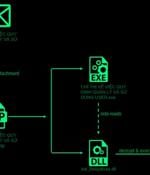
High-profile government and telecom entities in Asia have been targeted as part of an ongoing campaign since 2021 that's designed to deploy basic backdoors and loaders for delivering next-stage...

Permission Slip, an iPhone and Android app developed by Consumer Reports, helps users ask companies and data brokers to stop sharing their personal data and/or delete it. These laws allow the citizens of those states to demand that companies and data brokers that collected their personal information stop using it and delete it.

When American International Group launched the first cyber insurance policy in 1997, it stepped into completely unknown territory to gain market share. While in the UK adoption rates of cyber insurance vary significantly depending on the size of an organization, the US has seen a notable spike in demand across many markets for the past two years, with premiums increasing by 50% in 2022, in large part due to increasing ransomware attacks.
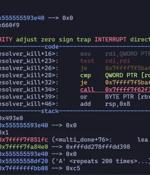
Patches have been released for two security flaws impacting the Curl data transfer library, the most severe of which could potentially result in code execution. The list of vulnerabilities is as...

In this Help Net Security interview, Charles d'Hondt, Head of Operations, Ambionics Security, talks about the necessity of implementing continuous penetration testing because yearly ones are not enough. Many organizations have been accustomed to annual penetration tests.

I serves as a unified platform to consolidate observables, indicators of compromise, TTPs, and threat-related knowledge. It enhances observables automatically, such as domain resolution and IP geolocation, saving you the effort.

Our cell phone is possibly even more vulnerable today than an experimental chip injected under the skin, since this chip, although susceptible to hacking, has a very limited function, while the cell phone is exposed to countless threats. "What can be hacked is the technology, not the body itself. A vulnerable device can be hacked both outside and inside the body. What we need to pay attention to is the security of the technology we are trying to implant," he points out.

74% of CEOs are concerned about their organizations' ability to avert or minimize damage to the business from a cyberattack - even though 96% of CEOs said that cybersecurity is critical to organizational growth and stability, according to Accenture. 60% of CEOs said their organizations don't incorporate cybersecurity into business strategies, services or products from the outset, and 44% believe cybersecurity requires episodic intervention rather than ongoing attention.