Security News > 2023 > April

QBot malware is now distributed in phishing campaigns utilizing PDFs and Windows Script Files to infect Windows devices. Qbot is a former banking trojan that evolved into malware that provides initial access to corporate networks for other threat actors.

Assuming that either your CSPM or SSPM will secure your company resources that live off-premises is misplaced trust in a security tool that was only designed to secure either your cloud or your SaaS stack. It's absolutely vital for decision makers to understand the difference between CSPM and SSPM, the value derived from each solution, and that both complement each other.

A new Android trojan called 'Chameleon' has been targeting users in Australia and Poland since the start of the year, mimicking the CoinSpot cryptocurrency exchange, an Australian government agency, and the IKO bank. The mobile malware was discovered by cybersecurity firm Cyble, which reports seeing distribution through compromised websites, Discord attachments, and Bitbucket hosting services.

A recruitment business that sent out an eye watering 107 million spam emails is now nursing a £130,000 fine from Britain's data watchdog. "It's an issue many of us face - opening up our email inboxes and it being filled with emails we did not ask for or consent to," said Andy Curry, ICO head of investigations.
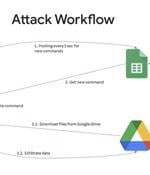
A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control amid broader abuse of Google's infrastructure for malicious ends. The starting point of the attack is a phishing email that contains links to a password-protected file hosted on Google Drive, which, in turn, incorporates the GC2 tool to read commands from Google Sheets and exfiltrate data using the cloud storage service.

The Deep, Dark Web - The Underground - is a haven for cybercriminals, teeming with tools and resources to launch attacks for financial gain, political motives, and other causes. Did you know that the underground also offers a goldmine of threat intelligence and information that can be harnessed to bolster your cyber defense strategies? The challenge lies in continuously monitoring the right dark web sources and gathering actionable intelligence through manual methods, which can lead to analyst fatigue and delayed action.

Motherboard has found, this synthesized call and another against Hempstead High School were just one small part of a months-long, nationwide campaign of dozens, and potentially hundreds, of threats made by one swatter in particular who has weaponized computer generated voices. Known as "Torswats" on the messaging app Telegram, the swatter has been calling in bomb and mass shooting threats against highschools and other locations across the country.

Nobody goes out and buys new firmware; there are plenty of enthusiast alternate firmware images for any number of devices, but these are almost all free and open source. While companies can buy in firmware from other companies, more often, as with MSI, you're a hardware company writing your own firmware.

Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool to fly under the radar and automate the process of exfiltrating data from compromised networks. "Threat actors using built-in data exfiltration methods like negate the need to bring in external tools that might be flagged by security software and/or human-based security detection mechanisms," Palo Alto Networks Unit 42 researcher Ryan Chapman said.

This week meet a reader we'll Regomize as "Wesley", who 25 years ago was about to embark on a thesis in mechanical engineering, continuing the work done by a more senior student who was working towards his doctorate. The senior student readily agreed, but the days passed, and Wesley still didn't have the data he needed.