Security News > 2023 > January

ESET researchers have discovered yet another wiper malware used to target Ukrainian organizations. Dubbed SwiftSlicer, it is thought to be wielded by the Sandworm APT. Simultaneously, the Ukranian CERT has confirmed that the attackers who recently aimed to disrupting the operation of the National News Agency of Ukraine used various wiper malware and one legitimate Windows command line utility to try to "Destroy" machines running different operating systems.

Passwords are a mess, MFA can be more of a stopgap than a solution to phishing and running your own public key infrastructure for certificates is a lot of work. Ironically, if you're a security-aware organization in a regulated industry that already did the hard work of adopting the previous gold standard - smartcards that hold a security certificate and validate it against a certificate authority on your infrastructure - you might find yourself stuck running ADFS as you try to move to the new FIDO keys.

Sports fashion retailer JD Sports has confirmed miscreants broke into a system that contained data on a whopping 10 million customers, but no payment information was among the mix. The data accessed consisted of customer name, billing address, delivery address, phone number, order details and the final four digits of payment cards "Of approximately 10 million unique customers."

Webinar It's a startling truth but 45 percent of workers in the US believe using public Wi-Fi is safe. At the same time, the 2021 Egress Insider Data Breach Survey found that a staggering 94 percent of organizations surveyed had suffered an insider data breach with human error the principal cause.

Critical vulnerabilities discovered in OpenEMR can be chained to gain code execution on a server running a vulnerable version of the popular open-source electronic health record system. Discovered, privately reported and now publicly documented by researcher Dennis Brinkrolf, the vulnerabilities have been promptly patched by the OpenEMR maintainers at the end of November 2022.

NIST is planning a significant update of its Cybersecurity Framework. At this point, it's asking for feedback and comments to its concept paper.

A U.S. No Fly list with over 1.5 million records of banned flyers and upwards of 250,000 'selectees' has been shared publicly on a hacking forum. BleepingComputer has confirmed the list is the same TSA No Fly list that was discovered recently on an unsecured CommuteAir server.
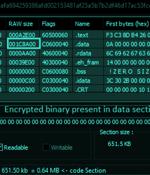
A new Golang-based information stealer malware dubbed Titan Stealer is being advertised by threat actors through their Telegram channel. Titan is offered as a builder, enabling customers to customize the malware binary to include specific functionalities and the kind of information to be exfiltrated from a victim's machine.

Current cybersecurity practices are woefully unprepared to meet the complexities of modern networks. Cloud services, remote users, personally-owned devices, mobile company assets and other forms of tech regularly move from outside the network in, and a once-safe device can't be assumed to be safe again.

According to Palo Alto Networks Unit 42, the ongoing campaign is said to have recorded 134 million exploit attempts as of December 2022, with 97% of the attacks occurring in the past four months. What's more, 95% of the attacks leveraging the security shortcoming that emanated from Russia singled out organizations in Australia.