Security News > 2022 > September > New EvilProxy Phishing Service Allowing Cybercriminals to Bypass 2-Factor Security
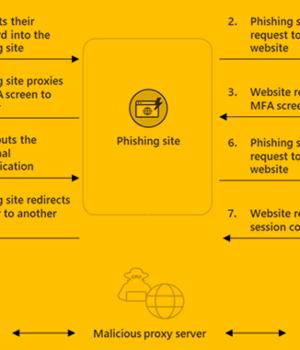
A new phishing-as-a-service toolkit dubbed EvilProxy is being advertised on the criminal underground as a means for threat actors to bypass two-factor authentication protections employed against online services.
"EvilProxy actors are using reverse proxy and cookie injection methods to bypass 2FA authentication - proxifying victim's session," Resecurity researchers said in a Monday write-up.
EvilProxy is similar to adversary-in-the-middle attacks in that users interact with a malicious proxy server that acts as a go-between for the target website, covertly harvesting the credentials and 2FA passcodes entered in the login pages.
Attacks against Google accounts, in contrast, cost up to $600 per month.
While the sale of EvilProxy to prospective customers is subject to vetting by the actors, it goes without saying that the service offers a "Cost-effective and scalable solution" to carry out social engineering attacks.
The development is further an indication that adversaries are upgrading their attack arsenal to orchestrate sophisticated phishing campaigns targeting users in a manner that can defeat existing security safeguards.
News URL
https://thehackernews.com/2022/09/new-evilproxy-phishing-service-allowing.html