Security News > 2022 > August

Google wants to improve the security of its open source projects and those projects' third-party dependencies by offering rewards for bugs found in them. Google offers rewards for bugs in its open source software.
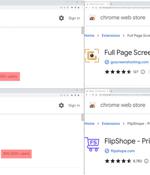
Five imposter extensions for the Google Chrome web browser masquerading as Netflix viewers and others have been found to track users' browsing activity and profit of retail affiliate programs. "The extensions offer various functions such as enabling users to watch Netflix shows together, website coupons, and taking screenshots of a website," McAfee researchers Oliver Devane and Vallabh Chole said.

A persistent Golang-based malware campaign dubbed GO#WEBBFUSCATOR has leveraged the deep field image taken from NASA's James Webb Space Telescope as a lure to deploy malicious payloads on infected systems. Phishing emails containing a Microsoft Office attachment act as the entry point for the attack chain that, when opened, retrieves an obfuscated VBA macro, which, in turn, is auto-executed should the recipient enable macros.

Jamf Threat Defense protects against mobile endpoint threat vectors through a highly effective mobile application, the Jamf Trust app, and prevents in-network threats in real-time through Jamf's Secure Access Layer. Jamf Threat Defense accommodates all device types and ownership models while safeguarding user privacy.

Organizations are struggling to sufficiently secure new cloud environments implemented during the pandemic, while maintaining legacy equipment and trying to adapt their overall security strategy to the evolving landscape, according to a Proofpoint study released in collaboration with The Cloud Security Alliance reveals. This Help Net Security video highlights how organizations adopt cloud infrastructures to support their remote and hybrid work environments.

Google on Monday introduced a new bug bounty program for its open source projects, offering payouts anywhere from $100 to $31,337 to secure the ecosystem from supply chain attacks. Called the Open Source Software Vulnerability Rewards Program, the offering is one of the first open source-specific vulnerability programs.

The campaign, active from April to June of this year, targeted Australian government agencies, Australian media companies and manufacturers who conduct maintenance on wind turbine fleets in the South China Sea. According to the researchers, victims were sent phishing emails that directed them to faked versions of Australian news outlets The Herald Sun and The Australian.

To automate the collection of massive amounts of web data, security teams and departments rely on web data collection networks. Web data collection platforms and proxy networks allow security firms and operators to gain access to multiple different data sources - and receive accurate depictions of what is present on these websites - all at once and in real time.

Several U.S. states have recently moved to ban local and state agencies and organizations funded by taxpayers' dollars from paying off ransomware gangs, and a few more are gearing up to it. In this Help Net Security video interview, Alex Iftimie, Partner at Morrison & Foerster, talks about the possible repercussions of such legislation and, in general, about the evolving nature of ransomware attacks and the current global efforts aimed at fighting the ransomware threats.

A vulnerability assessment is a methodical examination of network infrastructure, computer systems, and software with the goal of identifying and addressing known security flaws. Usually, the vulnerability scanning tool also provides instructions on how to remediate or mitigate the discovered flaws.