Security News > 2022 > July

Due to these factors, organizations are searching for new methods of risk assessment to better evaluate the market for cyberinsurance, per Panaseer's "2022 Cyber Insurance Market Trends Report". "The core exercise in assessing cyber risk for insurance purposes continues to be quantifying the probability and financial impact of cyber threats."

The findings, which NJIT researchers will present at the Usenix Security Symposium in Boston next month, show how an attacker who tricks someone into loading a malicious website can determine whether that visitor controls a particular public identifier, like an email address or social media account, thus linking the visitor to a piece of potentially personal data. When you visit a website, the page can capture your IP address, but this doesn't necessarily give the site owner enough information to individually identify you.

Amazon-owned home security company Ring turned over footage to US law enforcement without permission from the devices' owners 11 times so far in 2022, according to details unveiled by Massachusetts senator Ed Markey. Despite Amazon policy that police cannot view recordings without owners' explicit permission, that policy does not apply to subpoenas and emergency requests - which is exactly what Amazon said happened in these 11 cases, although it seems the judge of what constitutes emergency request is left up to Ring itself.

While the Twitter API status page shows no issues for today, almost 55,000 users have reported over the past 30 minutes that that the service is not working. At the time of writing, the browser version of the Twitter app is showing the typical "Something went wrong, but don't fret - it's not your fault" errors.

Although there is a greater awareness of cybersecurity threats than ever before, it is becoming increasingly difficult for IT departments to get their security budgets approved. There are some things that IT pros can do to improve the chances of getting their security budgets approved.

By misusing the PayPal logo and general design, the phishing kit leads users through a set of pages and forms aimed at collecting information that can later be used to steal the victims' identity and perform money laundering, open cryptocurrency accounts, make fraudulent tax return claims, and much more. The attackers using the kit are targeting legitimate WordPress sites.

The short notice given by the exchange via a private email left some customers suspecting if this was an "Exit scam" or caused by another mysterious incident. Crypto platform shut down: 5 days left to take out funds.

Media organizations and journalists in the last years have been increasingly targeted by state-sponsored advanced persistent threat actors with a clear purpose: Obtain access to their sensitive information, spy their activities or even identify their sources. Zirconium, a threat actor also known as TA412, has been targeting American journalists since 2021.

The advanced persistent threat group known as Transparent Tribe has been attributed to a new ongoing phishing campaign targeting students at various educational institutions in India at least since December 2021. Also tracked under the monikers APT36, Operation C-Major, PROJECTM, Mythic Leopard, the Transparent Tribe actor is suspected to be of Pakistani origin and is known to strike government entities and think tanks in India and Afghanistan with custom malware such as CrimsonRAT, ObliqueRAT, and CapraRAT. But the targeting of educational institutions and students, first observed by India-based K7 Labs in May 2022, indicates a deviation from the adversary's typical focus.
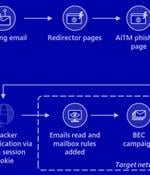
Microsoft on Tuesday disclosed that a large-scale phishing campaign targeted over 10,000 organizations since September 2021 by hijacking Office 365's authentication process even on accounts secured with multi-factor authentication. The intrusions entailed setting up adversary-in-the-middle phishing sites, wherein the adversary deploys a proxy server between a potential victim and the targeted website so that recipients of a phishing email are redirected to lookalike landing pages designed to capture credentials and MFA information.