Security News > 2022 > February

Microsoft 365 has all the tools you need to run your organization in the cloud, from personal productivity to group collaboration, to advanced analytics and security management. While it does include compliance and policy tools, it doesn't claim to offer a full set of data recovery tools.

The Medusa Android banking Trojan is seeing increased infection rates as it targets more geographic regions to steal online credentials and perform financial fraud. Today, researchers at ThreatFabric have published a new report detailing the latest tricks employed by the Medusa malware and how it continues to evolve with new features.

Microsoft says it has fixed a known issue triggered by last month's Windows updates that would cause apps using Microsoft. "After installing updates released January 11, 2022 or later, apps using Microsoft.NET Framework to acquire or set Active Directory Forest Trust Information might fail, close, or you might receive an error from the app or Windows," Microsoft explained in an update to the Windows health dashboard.

The Roaming Mantis SMS phishing campaign has finally reached Europe, as researchers detect campaigns targeting Android and iPhone users in Germany and France with malicious apps and phishing pages. Roaming Mantis is a credential theft and malware distribution campaign that uses SMS phishing to distribute malicious Android apps as standalone APK files outside the Google Play Store.

The recent growth in popularity of phishing kits that bypass MFA protection show that attackers have taken note of it and are adapting. Microsoft's inaugural Cyber Signals report shows, on the other hand, that only 22 percent of customers using Microsoft Azure Active Directory have implemented MFA protection.

This article looks at three real-life attacks attempted via corporate email, all of which were stopped by Group-IB's cloud email protection system Atmosphere. Email domains of major corporations, solutions providers, and government entities are considered safe - provided they have passed sender address verification - which is why most emails from them are delivered without additional analysis.

It's important that your current security awareness efforts are appropriate for how your employees work today, not how they worked two years ago. The strongest security cultures are those where each employee fully understands that they are on the front lines.

In the wake of the SolarWinds and Kaseya attacks, third-party cybersecurity risks remain top of mind for security leaders. Third-party SaaS vendors have permeated every facet of our workflows and enmeshed itself across enterprise environments.

Critical Insight announced the release of a report which analyzes ??breach data reported to the U.S. Department of Health and Human Services by healthcare organizations. The effects of braches on healthcare organizations Total individuals affected: 2021 hit a high of 45 million individuals affected by healthcare attacks, up from 34 million in 2020.
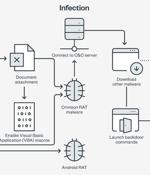
A politically motivated advanced persistent threat group has expanded its malware arsenal to include a new remote access trojan in its espionage attacks aimed at Indian military and diplomatic entities. Called CapraRAT by Trend Micro, the implant is an Android RAT that exhibits a high "Degree of crossover" with another Windows malware known as CrimsonRAT that's associated with Earth Karkaddan, a threat actor that's also tracked under the monikers APT36, Operation C-Major, PROJECTM, Mythic Leopard, and Transparent Tribe.