Security News > 2022 > January
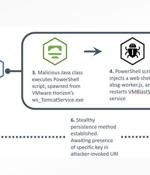
The digital security team at the U.K. National Health Service has raised the alarm on active exploitation of Log4Shell vulnerabilities in unpatched VMware Horizon servers by an unknown threat actor to drop malicious web shells and establish persistence on affected networks for follow-on attacks. "The attack likely consists of a reconnaissance phase, where the attacker uses the Java Naming and Directory InterfaceTM via Log4Shell payloads to call back to malicious infrastructure," the non-departmental public body said in an alert.

The most noteworthy information that came out today is a new FBI flash alert warning that REvil and BlackMatter were sending malicious USB drives to defense firms that deployed ransomware. Lapsus$ ransomware gang hits SIC, Portugal's largest TV channel The Lapsus$ ransomware gang has hacked and is currently extorting Impresa, the largest media conglomerate in Portugal and the owner of SIC and Expresso, the country's largest TV channel and weekly newspaper, respectively.

Besides the difficulty of tracking down all instances of the ubiquitous Apache logging library, the job of patching the flaws has been further complicated for many agencies by end-of-life and end-of-support systems connected to the network. Due to network-connected EoL and EoS systems: an issue that's further complicated by pandemic-wrought supply chain delays and remote-work issues.

The price of squid in Korea is rising due to limited supply. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered.

SonicWall has confirmed today that some of its Email Security and firewall products have been hit by the Y2K22 bug, causing message log updates and junk box failures starting with January 1st, 2022. The company says that email users and administrators will no longer be able to access the junk box or un-junk newly received emails on affected systems.

FCI's data breach notice said that the healthcare organization first detected suspicious activity on its internal systems on Feb. 1, 2021. The data of more than 3,300 U.S. military service members, military dependents and civilians employed by the DoD were compromised as part of what turned out to be a transnational cybercrime ring created to defraud them out of $1.5 million in military benefits from the DoD and the VA. With regards to the FCI breach, the organization said that it immediately took steps to eliminate unauthorized access and brought in independent forensic investigators to investigate and remediate the matter, on top of additional security measures meant to further secure access to data, individual accounts, and equipment, including the implementation of enterprise identity verification software.

This time, the bug isn't in Apache's beleagured Log4j toolkit, but can be found in a popular Java SQL server called the H2 Database Engine. As a result, you can bundle the H2 SQL database code right into your own Java apps, and run your databases entirely in memory, with no need for separate server processes.

A threat group that identifies itself as Uawrongteam is dumping data stolen from FlexBooker - a popular online appointment scheduling tool for booking services ranging from counseling to haircuts - on a cybercriminal forum. The data from FlexBooker is being offered up by Uawrongteam, along with other databases stolen on the same day, Dec. 23, from Racing.com and Redbourne Group's rediCASE case management software, BleepingComputer reported.

The Federal Bureau of Investigation warned US companies in a recently updated flash alert that the financially motivated FIN7 cybercriminal group targeted the US defense industry with packages containing malicious USB devices to deploy ransomware. The attackers mailed packages containing 'BadUSB' or 'Bad Beetle USB' devices with the LilyGO logo, commonly available for sale on the Internet.

The Federal Bureau of Investigation warned US companies in a recently updated flash alert that the financially motivated FIN7 cybercriminals group is targeting the US defense industry with packages containing malicious USB devices. The packages have been mailed via the United States Postal Service and United Parcel Service to businesses in the transportation and insurance industries since August 2021 and defense firms starting with November 2021.