Security News > 2022 > January > Iranian Hackers Exploit Log4j Vulnerability to Deploy PowerShell Backdoor
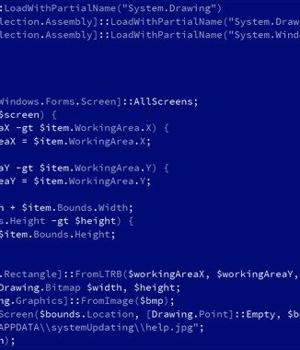
An Iranian state-sponsored actor has been observed scanning and attempting to abuse the Log4Shell flaw in publicly-exposed Java applications to deploy a hitherto undocumented PowerShell-based modular backdoor dubbed "CharmPower" for follow-on post-exploitation.
Log4Shell aka CVE-2021-44228 concerns a critical security vulnerability in the popular Log4j logging library that, if successfully exploited, could lead to remote execution of arbitrary code on compromised systems.
The ease of the exploitation coupled with the widespread use of Log4j library has created a vast pool of targets, even as the shortcoming has attracted swarms of bad actors, who have seized on the opportunity to stage a dizzying array of attacks since its public disclosure last month.
While Microsoft previously pointed out APT35's efforts to acquire and modify the Log4j exploit, the latest findings show that the hacking group has operationalized the flaw to distribute the PowerShell implant capable of retrieving next-stage modules and exfiltrating data to a command-and-control server.
What's more, Hafnium, another threat actor group operating out of China, has also been observed utilizing the vulnerability to attack virtualization infrastructure to extend their typical targeting, Microsoft noted.
"Judging by their ability to take advantage of the Log4j vulnerability and by the code pieces of the CharmPower backdoor, the actors are able to change gears rapidly and actively develop different implementations for each stage of their attacks," the researchers said.
News URL
https://thehackernews.com/2022/01/iranian-hackers-exploit-log4j.html
Related news
- Hackers exploit WordPress plugin auth bypass hours after disclosure (source)
- Hackers exploit old FortiGate vulnerabilities, use symlink trick to retain limited access to patched devices (source)
- Kimsuky Exploits BlueKeep RDP Vulnerability to Breach Systems in South Korea and Japan (source)
- Russian Hackers Exploit Microsoft OAuth to Target Ukraine Allies via Signal and WhatsApp (source)
- Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Hackers Exploit Samsung MagicINFO, GeoVision IoT Flaws to Deploy Mirai Botnet (source)
- Hackers exploit OttoKit WordPress plugin flaw to add admin accounts (source)
- Chinese Hackers Exploit SAP RCE Flaw CVE-2025-31324, Deploy Golang-Based SuperShell (source)
- Türkiye Hackers Exploited Output Messenger Zero-Day to Drop Golang Backdoors on Kurdish Servers (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2021-12-10 | CVE-2021-44228 | Deserialization of Untrusted Data vulnerability in multiple products Apache Log4j2 2.0-beta9 through 2.15.0 (excluding security releases 2.12.2, 2.12.3, and 2.3.1) JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. network low complexity siemens apache intel debian fedoraproject sonicwall netapp cisco snowsoftware bentley percussion apple CWE-502 critical | 10.0 |