Security News

The warnings have at least one ransomware accoutrement that might look convincing at first blush: a countdown clock tick-tick-ticking away, warning site owners that they've got seven days, 10 hours, 21 minutes and 9 seconds to fork over 0.1 Bitcoin - about USD $6,000 at the time this story was posted - before the files are encrypted and go up in an irretrievable puff of e-smoke. Sucuri researchers who tracked down and analyzed the fake ransomware said they found a whole lot of nothing.

A new wave of attacks starting late last week has hacked close to 300 WordPress sites to display fake encryption notices, trying to trick the site owners into paying 0.1 bitcoin for restoration. The researchers discovered that the websites had not been encrypted, but rather the threat actors modified an installed WordPress plugin to display a ransom note and countdown when.

A high severity security flaw in the WP Reset PRO WordPress plugin can let authenticated attackers wipe vulnerable websites, as revealed by Patchstack security researchers. Subscriber is a default WordPress user role, often enabled to allow registered users to write comments on WordPress sites' comment section.

The OptinMonster plugin is affected by a high-severity flaw that allows unauthorized API access and sensitive information disclosure on roughly a million WordPress sites. OptinMonster is one of the most popular WordPress plugins used to create beautiful opt-in forms that help site owners convert visitors to subscribers/customers.

The flaw, found in the Hashthemes Demo Importer plugin, allows any authenticated user to exsanguinate a vulnerable WordPress site, deleting nearly all database content and uploaded media. Researchers have discovered a homicidal WordPress plugin that allows subscribers to wipe sites clean of content.

A high severity security flaw found in a WordPress plugin with more than 8,000 active installs can let authenticated attackers reset and wipe vulnerable websites. The plugin in question, known as Hashthemes Demo Importer, is designed to help admins import demos for WordPress themes with a single, without dealing with installing any dependencies.

Vulnerabilities in the Brizy Page Builder plugin for WordPress sites could be chained together to allow attackers to completely take over a website, according to researchers. The two fresh bugs can both be chained with the re-introduced access control vulnerability to allow complete site takeover, researchers explained.
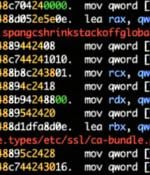
A recently discovered wave of malware attacks has been spotted using a variety of tactics to enslave susceptible machines with easy-to-guess administrative credentials to co-opt them into a network with the goal of illegally mining cryptocurrency. "The malware's primary tactic is to spread by taking advantage of vulnerable systems and weak administrative credentials. Once they've been infected, these systems are then used to mine cryptocurrency," Akamai security researcher Larry Cashdollar said in a write-up published last week.

According to a recent report from the Institute for Security and Technology, ransomware attacks cost businesses 21 days of downtime, on average. Because WordPress is the market share leader, my team of SOC analysts aren't strangers to responding to WordPress security issues.

Two vulnerabilities have been found in the Gutenberg Template Library & Redux Framework plugin for WordPress, which is installed on more than 1 million websites. It exists because the Gutenberg Template Library & Redux Framework plugin registers several AJAX actions available to unauthenticated users, one of which is deterministic and predictable, making it possible to uncover what the $support hash for a site would be.