Security News

Spammers have started using a tricky URL obfuscation technique that sidesteps detection - and ultimately infects victims with the LokiBot trojan. When the PowerPoint file is opened, the document attempts to access a URL via a Windows binary, and this leads to various malware being installed onto the system.

Southern Water - British supplier of the liquid of life - botched its internal Sharepoint implementation so badly that a customer was able to view other people's account details. Reg reader Chris H discovered that the way Southern Water had set up Sharepoint to host customer information as a "Your account" style section of their website exposed URLs that could be tweaked to view other people's account information.

Google announced on Wednesday that it's preparing to run an experiment in Chrome 86 as part of its fight against URL spoofing. Research conducted recently by Google and the University of Illinois at Urbana-Champaign showed that 60 percent of users were tricked when a URL path contained a misleading brand name.

An issue related to the Zoom feature that allows for the customization of meeting URLs could have been exploited for phishing attacks, Check Point reveals. The recently identified security issue, Check Point says, is related to the Zoom Vanity URL, a custom URL that organizations are required to use when looking to enable single sign-on.
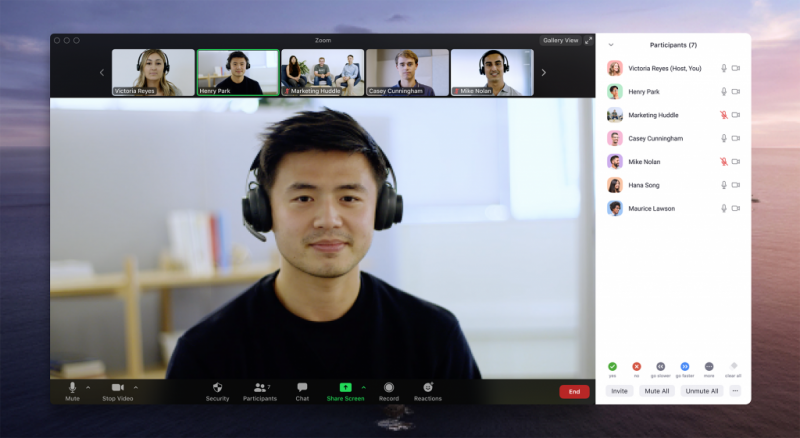
Disclosed by Zoom and Check Point on Thursday, the security flaw existed in the "Vanity URL" feature for Zoom, which allows companies to set up their won Zoom meeting domain, i.e. "Yourcompany.zoom.us." Companies can add customized logos and branding to the page, and end users access the page and click meeting links within that page to connect to a Zoom call. "A hacker could target such an interface and attempt to redirect a user to enter a meeting ID into the malicious Vanity URL rather than the actual or genuine Zoom web interface. As with the direct links attacks, without careful cybersecurity training, a victim of such attacks may not have been able to recognize the malicious URL and have fallen prey to the attack."

Massively popular video conferencing platform Zoom has worked with cybersecurity company Check Point to resolve a glaring security issue centered on vanity URLs. Check Point researchers Adi Ikan, Liri Porat, and Ori Hamama said in a study that they worked with Zoom to identify two ways cybercriminals could exploit the widely used feature.

Working remotely from home has become a reality for millions of people around the world, putting pressure on IT and security teams to ensure that remote employees not only remain as productive as possible, but also that they keep themselves and corporate data as secure as possible. Even less so in the case of BYOD. Remote workers attempting to access risky content.

The Brave browser has provoked unhappiness among some of its users after being caught redirecting searches to affiliate links that earned it commission. What this means is that Brave users searching for Binance, a cryptocurrency exchange, would have had their query autocompleted so that they ended up on a special version of the Binance homepage that lets the company know that Brave's address bar was the origin of that visit.

That's especially true with phishing emails that attempt to hide the source of their deceptive landing pages and spoof or reference a well-known company or brand. A new phishing attack analyzed by Armorblox takes advantage of Symantec to trick users into falling for the scam.

Enough people must have griped about the loss of "Www" and "Https" in Chrome's address bar to make Google rethink it: Chromium developers are testing a new Omnibox context menu that would give users the option to "Always Show Full URLs.". On 17 March, Chromium developers outlined the plan for users to opt-out of URL snippage in a post on the bug tracker titled "Implement Omnibox context menu option to always show full URLs".