Security News

A change in the deployment of the RomCom malware strain has illustrated the blurring distinction between cyberattacks motivated by money and those fueled by geopolitics, in this case Russia's illegal invasion of Ukraine, according to Trend Micro analysts. The infosec vendor pointed out that RomCom's operators, threat group Void Rabisu, also has links to the notorious Cuba ransomware, and therefore assessed it was assumed to be a financially driven criminal organization.

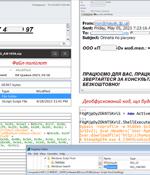
The Computer Emergency Response Team of Ukraine has warned of cyber attacks targeting state bodies in the country as part of an espionage campaign. In the attack chain described by the agency, the emails targeted an unspecified ministry and purported to be from the Embassy of Tajikistan in Ukraine.
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, according to the Computer Emergency Response Team of Ukraine. In a related advisory, Ukraine's cybersecurity authority also revealed details of destructive attacks orchestrated by a group known as UAC-0165 against public sector organizations.

Finish newspaper Helsinin Sanomat has created a custom Counter-Strike: Global Offensive map explicitly made to bypass Russian news censorship and smuggle information about the war in Ukraine to Russian players. Starting in March 2022, following its invasion of Ukraine, Russia began blocking international news outlets to implement tighter controls over what news reaches the Russian audience regarding the ongoing war.

The Russian 'Sandworm' hacking group has been linked to an attack on Ukrainian state networks where WinRar was used to destroy data on government devices. In a new advisory, the Ukrainian Government Computer Emergency Response Team says the Russian hackers used compromised VPN accounts that weren't protected with multi-factor authentication to access critical systems in Ukrainian state networks.
The Kremlin-backed threat group APT28 is flooding Ukrainian government agencies with email messages about bogus Windows updates in the hope of dropping malware that will exfiltrate system data. Executing the command simulates a Windows update but actually downloads and executes a PowerShell script that collects basic system information about using such commands as "Tasklist" and "Systeminfo".

Google's Threat Analysis Group has been monitoring and disrupting Russian state-backed cyberattacks targeting Ukraine's critical infrastructure in 2023. Google reports that from January to March 2023, Ukraine received roughly 60% of the phishing attacks originating from Russia, making it the most prominent target.

Elite hackers associated with Russia's military intelligence service have been linked to large-volume phishing campaigns aimed at hundreds of users in Ukraine to extract intelligence and influence public discourse related to the war. The latest intrusion set, starting in early February 2023, involved the use of reflected cross-site scripting attacks in various Ukrainian government websites to redirect users to phishing domains and capture their credentials.

The Cyber Police of Ukraine, in collaboration with law enforcement officials from Czechia, has arrested several members of a cybercriminal gang that set up phishing sites to target European users. The suspects are alleged to have created more than 100 phishing portals aimed at users in France, Spain, Poland, Czechia, Portugal, and other nations in the region.

A cyber espionage campaign targeting organizations in Russian-occupied regions of Ukraine is using novel malware to steal data, according to Russia-based infosec software vendor Kaspersky. In a report published Tuesday, Kaspersky researchers detailed the infections, which use a PowerShell-based backdoor they've named "PowerMagic" and a previously unknown framework dubbed "CommonMagic" that can steal files from USB devices, take screenshots every three seconds, and send all of this data back to the attacker.