Security News

Food delivery firm DoorDash has disclosed a data breach exposing customer and employee data that is linked to the recent cyberattack on Twilio. DoorDash previously suffered a data breach in 2019 that exposed the data of nearly 5 million customers.

Food delivery firm DoorDash has disclosed a data breach exposing customer and employee data that is linked to the recent cyberattack on Twilio. In a security advisory released Thursday afternoon, DoorDash says that a threat actor gained access to the company's internal tools using stolen credentials from a third-party vendor that had access to their systems.

Twilio's investigation into the attack on August 4 reveals that hackers gained access to some Authy user accounts and registered unauthorized devices. Authy is a two-factor authentication service from Twilio that allows users to secure their online accounts where the feature is supported by identifying a second time via a dedicated app after typing in the login credentials.

Criminals behind the cyberattack attempts on Twilio and Cloudflare earlier this month had cast a much wider net in their phishing expedition, targeting as many as 135 organizations - primarily IT, software development and cloud services providers based in the US. The gang went after the employees of Okta customers, sending victims text messages with malicious links to sites spoofing their company's authentication page to harvest their work login credentials and multi-factor authentication codes. In research published Thursday, the threat intel team revealed the Oktapus phishing trip, which began in March, snaffled 9,931 user credentials and 5,441 multi-factor authentication codes.

Group-IB has discovered that the recently disclosed phishing attacks on the employees of Twilio and Cloudflare were part of the massive phishing campaign that resulted in 9,931 accounts of over 130 organizations being compromised. Group-IB Threat Intelligence team uncovered and analyzed the attackers' phishing infrastructure, including phishing domains, the phishing kit as well as the Telegram channel controlled by the threat actors to drop compromised information.

Hackers responsible for a string of recent cyberattacks, including those on Twilio, MailChimp, Cloudflare, and Klaviyo, compromised over 130 organizations in the same phishing campaign. This phishing campaign utilized a phishing kit codenamed '0ktapus' to steal 9,931 login credentials that the hackers then used to gain access to corporate networks and systems through VPNs and other remote access devices.
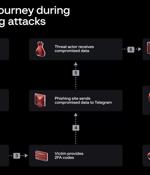
The threat actor behind the attacks on Twilio and Cloudflare earlier this month has been linked to a broader phishing campaign aimed at 136 organizations that resulted in a cumulative compromise of 9,931 accounts. The activity has been condemned 0ktapus by Group-IB because the initial goal of the attacks was to "Obtain Okta identity credentials and two-factor authentication codes from users of the targeted organizations."

All users can rest assured that their message history, contact lists, profile information, whom they'd blocked, and other personal data remain private and secure and were not affected. For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal.

Signal - considered one of the better secured of all the encrypted messaging apps - claims the attacker would not have been able to access the message history, contact lists, profile information, or other personal data associated with these user accounts. According to Signal's security note, when Twilio was hit by a phishing attack earlier this month, this may potentially have led to the phone number of 1,900 Signal users being revealed as registered to a specific Signal account.

The attacker behind the recent Twilio data breach may have accessed phone numbers and SMS registration codes for 1,900 users of the popular secure messaging app Signal. "Among the 1,900 phone numbers, the attacker explicitly searched for three numbers, and we've received a report from one of those three users that their account was re-registered," the Signal team shared on Monday.