Security News
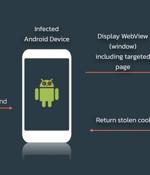
A mix of banking applications, cryptocurrency wallets, and shopping apps from the U.S. and Spain are the target of a newly discovered Android trojan that could enable attackers to siphon personally identifiable information from infected devices, including banking credentials and open the door for on-device fraud. Dubbed S.O.V.A., the current version of the banking malware comes with myriad features to steal credentials and session cookies through web overlay attacks, log keystrokes, hide notifications, and manipulate the clipboard to insert modified cryptocurrency wallet addresses, with future plans to incorporate on-device fraud through VNC, carry out DDoS attacks, deploy ransomware, and even intercept two-factor authentication codes.

"The Trojan Triada snuck into one of these modified versions of the messenger called FMWhatsApp 16.80.0 together with the advertising software development kit," researchers from Russian cybersecurity firm Kaspersky said in a technical write-up published Tuesday. Modified versions of legitimate Android apps - a practice called Modding - are designed to perform functions not originally conceived or intended by the app developers.

"The Trojan Triada snuck into one of these modified versions of the messenger called FMWhatsApp 16.80.0 together with the advertising software development kit," researchers from Russian cybersecurity firm Kaspersky said in a technical write-up published Tuesday. Modified versions of legitimate Android apps - aka Modding - are designed to perform functions not originally conceived or intended by the app developers, and FMWhatsApp allows users to customize the app with different themes, personalize icons, and hide features like last seen, and even deactivate video calling features.
A new social engineering-based malvertising campaign targeting Japan has been found to deliver a malicious application that deploys a banking trojan on compromised Windows machines to steal credentials associated with cryptocurrency accounts. The application masquerades as an animated porn game, a reward points application, or a video streaming application, Trend Micro researchers Jaromir Horejsi and Joseph C Chen said in an analysis published last week, attributing the operation to a threat actor it tracks as Water Kappa, which was previously found targeting Japanese online banking users with the Cinobi trojan by leveraging exploits in Internet Explorer browser.

A newly discovered Android banking Trojan relies on screen recording and keylogging instead of HTML overlays for the capturing of login credentials, according to security researchers at ThreatFabric. ThreatFabric said the mobile malware leverages the Accessibility Services to identify the application running in the foreground and, if the app is in the target list, the malware starts screen recording.

Our story takes place a few years ago and concerns "Ruud" who had joined a very well-known company as head of IT. As befitted a person of his job title, Ruud had started putting the company's house in order and begun rolling out some standard security tools "To get us to a decent baseline." Leading from the front, Ruud dived in to do his bit.

An advanced persistent threat actor has been tracked in a new campaign deploying Android malware via the Syrian e-Government Web Portal, indicating an upgraded arsenal designed to compromise victims. "To the best of our knowledge, this is the first time that the group has been publicly observed using malicious Android applications as part of its attacks," Trend Micro researchers Zhengyu Dong, Fyodor Yarochkin, and Steven Du said in a technical write-up published Wednesday.

Spanish law enforcement agencies on Wednesday arrested 16 individuals belonging to a criminal network in connection with operating two banking trojans as part of a social engineering campaign targeting financial institutions in Europe. As part of an effort to lend credibility to their phishing attacks, the operators worked by sending emails under the guise of legitimate package delivery services and government entities such as the Treasury, urging the recipients to click on a link that stealthily downloaded malicious software onto the systems.

The TrickBot trojan is adding man-in-the-browser capabilities for stealing online banking credentials that resemble Zeus, the early banking trojan, researchers said - potentially signaling a coming onslaught of fraud attacks. According to researchers at Kryptos Logic Threat Intelligence, this functionality is carried out by TrickBot's webinject module.

Researchers have seen a new variant of the IcedID banking trojan sliding in via two new spam campaigns. ZIP files full of the malware - or links to such ZIP files - the new twist on the old banking trojan is a tweaked downloader, which the threat actors moved from the initial x86 version to the latest: an x86-64 version.