Security News

A large-scale malware campaign on Huawei's AppGallery has led to approximately 9,300,000 installs of Android trojans masquerading as over 190 different apps. Those who installed the apps on their devices will still have to remove them from their Android devices manually.

The BrazKing Android banking trojan has returned with dynamic banking overlays and a new implementation trick that enables it to operate without requesting risky permissions. RAT capabilities-BrazKing can manipulate the target banking application by tapping buttons or keying text in.
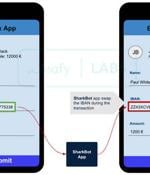
Cybersecurity researchers on Monday took the wraps off a new Android trojan that takes advantage of accessibility features on the devices to siphon credentials from banking and cryptocurrency services in Italy, the U.K., and the U.S. Dubbed "SharkBot" by Cleafy, the malware is designed to strike a total of 27 targets - counting 22 unnamed international banks in Italy and the U.K. as well as five cryptocurrency apps in the U.S. - at least since late October 2021 and is believed to be in its early stages of development, with no overlaps found to that of any known families. "The main goal of SharkBot is to initiate money transfers from the compromised devices via Automatic Transfer Systems technique bypassing multi-factor authentication mechanisms," the researchers said in a report.

A stealthier batch file with at least two layers of obfuscation;. ZIP file, the aforementioned stealthy batch file executes.

A new version of a banking trojan known as Mekotio is being deployed in the wild, with malware analysts reporting that it's using a new, stealthier infection flow. The last notable activity of Mekotio dates back to the summer of 2020 when the trojan's operators deployed it in a campaign targeting Latin American countries.
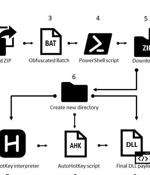
The operators behind the Mekotio banking trojan have resurfaced with a shift in its infection flow so as to stay under the radar and evade security software, while staging nearly 100 attacks over the last three months. The development comes after Spanish law enforcement agencies in July 2021 arrested 16 individuals belonging to a criminal network in connection with operating Mekotio and another banking malware called Grandoreiro as part of a social engineering campaign targeting financial institutions in Europe.
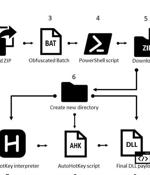
The operators behind the Mekotio banking trojan have resurfaced with a shift in its infection flow so as to stay under the radar and evade security software, while staging nearly 100 attacks over the last three months. The development comes after Spanish law enforcement agencies in July 2021 arrested 16 individuals belonging to a criminal network in connection with operating Mekotio and another banking malware called Grandoreiro as part of a social engineering campaign targeting financial institutions in Europe.

Cambridge University researchers have detailed a new way targeted vulnerabilities can be introduced into source code while making them invisible to human code reviewers, allowing for extensive supply-chain attacks. "We have discovered ways of manipulating the encoding of source code files so that human viewers and compilers see different logic. One particularly pernicious method uses Unicode directionality override characters to display code as an anagram of its true logic," professor Ross Anderson explained.

A novel class of vulnerabilities could be leveraged by threat actors to inject visually deceptive malware in a way that's semantically permissible but alters the logic defined by the source code, effectively opening the door to more first-party and supply chain risks. Dubbed "Trojan Source attacks," the technique "Exploits subtleties in text-encoding standards such as Unicode to produce source code whose tokens are logically encoded in a different order from the one in which they are displayed, leading to vulnerabilities that cannot be perceived directly by human code reviewers," Cambridge University researchers Nicholas Boucher and Ross Anderson said in a newly published paper.

Academic researchers have released details about a new attack method they call "Trojan Source" that allows injecting vulnerabilities into the source code of a software project in a way that human reviewers can't detect. "The trick is to use Unicode control characters to reorder tokens in source code at the encoding level," reveals Nicholas Boucher, one of the researchers that discovered Trojan Source.