Security News

The Emotet malware delivery botnet is back, almost a year after law enforcement agencies bragged about shutting it down and arresting the operators. The revival of Emotet is serious because in its final form the Windows malware network was increasingly being used to deliver ransomware, as well as the traditional online banking credential-stealing code it was previously best known for.

Emotet, one of the most prolific and disruptive botnet malware-delivery systems, appears to be making a comeback after nearly a year of inactivity, researchers have found. "TrickBot launched what appears to be the newer Emotet loader."
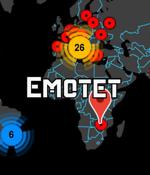
The Emotet malware was considered the most widely spread malware in the past, using spam campaigns and malicious attachments to distribute the malware.Emotet would then use infected devices to perform other spam campaigns and install other payloads, such as the QakBot and Trickbot malware.
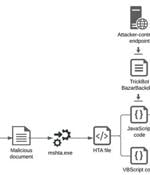
The operators of TrickBot trojan are collaborating with the Shathak threat group to distribute their wares, ultimately leading to the deployment of Conti ransomware on infected machines. "The implementation of TrickBot has evolved over the years, with recent versions of TrickBot implementing malware-loading capabilities," Cybereason security analysts Aleksandar Milenkoski and Eli Salem said in a report analysing recent malware distribution campaigns undertaken by the group.

A threat actor tracked as Shatak recently partnered with the ITG23 gang to deploy Conti ransomware on targeted systems. The Shatak operation partners with other malware developers to create phishing campaigns that download and infect victims with malware.

A Russian national, who was arrested in South Korea last month and extradited to the U.S. on October 20, appeared in a federal court in the state of Ohio on Thursday to face charges for his alleged role as a member of the infamous TrickBot group. Starting its roots as a banking trojan in 2016, TrickBot has evolved into a modular, multi-stage Windows-based crimeware solution capable of pilfering valuable personal and financial information, and even dropping ransomware and post-exploitation toolkits on compromised devices.

The US Department of Justice claims it's arrested a member of a gang that deployed the Trickbot ransomware. A heavily-redacted indictment names Vladimir Dunaev as a developer of the malware, and alleges he was "a Malware Developer for the Trickbot Group, overseeing the creation of internet browser injection, machine identification, and data harvesting codes used by the Trickbot malware".

A Russian national believed to be a member of the TrickBot malware development team has been extradited to the U.S. and is currently facing charges that could get him 60 years in prison. He is the second malware developer associated with the TrickBot gang that the Department of Justice arrested this year.

The development also speaks to the TrickBot gang's increasing sophistication and standing in the cybercrime underground, IBM researchers said: "This latest development demonstrates the strength of its connections within the cybercriminal ecosystem and its ability to leverage these relationships to expand the number of organizations infected with its malware." According to IBM, the TrickBot gang has now added powerful additional distribution tactics to its bag of tricks, thanks to the two new affiliates.

The operators behind the pernicious TrickBot malware have resurfaced with new tricks that aim to increase its foothold by expanding its distribution channels, ultimately leading to the deployment of ransomware such as Conti. The threat actor, tracked under the monikers ITG23 and Wizard Spider, has been found to partner with other cybercrime gangs known Hive0105, Hive0106, and Hive0107, adding to a growing number of campaigns that the attackers are banking on to deliver proprietary malware, according to a report by IBM X-Force.