Security News

Three popular npm packages, @rspack/core, @rspack/cli, and Vant, were compromised through stolen npm account tokens, allowing threat actors to publish malicious versions that installed cryptominers. [...]

The Internet Archive was breached again, this time on their Zendesk email support platform after repeated warnings that threat actors stole exposed GitLab authentication tokens. [...]

An X account hacking spree has fueled a successful pump-and-dump scheme for the $HACKED Solana token, with people rushing to buy the coin. [...]

Multiple high-profile open-source projects, including those from Google, Microsoft, AWS, and Red Hat, were found to leak GitHub authentication tokens through GitHub Actions artifacts in CI/CD...

Cybersecurity researchers from JFrog recently discovered a GitHub Personal Access Token in a public Docker container hosted on Docker Hub, which granted elevated access to the GitHub repositories of the Python language, Python Package Index, and the Python Software Foundation. The implications of someone finding this leaked token could be extremely severe.
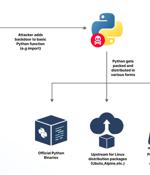
Cybersecurity researchers said they discovered an accidentally leaked GitHub token that could have granted elevated access to the GitHub repositories of the Python language, Python Package Index, and the Python Software Foundation repositories. JFrog, which found the GitHub Personal Access Token, said the secret was leaked in a public Docker container hosted on Docker Hub.

JetBrains warned customers to patch a critical vulnerability that impacts users of its IntelliJ integrated development environment apps and exposes GitHub access tokens. "In particular, malicious content as part of a pull request to a GitHub project which would be handled by IntelliJ-based IDEs, would expose access tokens to a third-party host."

JetBrains has fixed a critical vulnerability that could expose users of its integrated development environments to GitHub access token compromise. CVE-2024-37051 is a vulnerability in the JetBrains GitHub plugin on the IntelliJ open-source platform, and affects all IntelliJ-based IDEs as of 2023.1 onwards that have it enabled and configured/in-use.

Internal source code and data belonging to The New York Times was leaked on the 4chan message board after being stolen from the company's GitHub repositories in January 2024, The Times confirmed to BleepingComputer. "Basically all source code belonging to The New York Times Company, 270GB," reads the 4chan forum post.

AI platform Hugging Face says that its Spaces platform was breached, allowing hackers to access authentication secrets for its members. Hugging Face Spaces is a repository of AI apps created and submitted by the community's users, allowing other members to demo them.