Security News

SubSnipe is an open-source, multi-threaded tool to help find subdomains vulnerable to takeover. It's simpler, produces better output, and has more fingerprints than other subdomain takeover tools.

Researchers found half a dozen vulnerabilities of varying severity impacting Netgear WNR614 N300, a budget-friendly router that proved popular among home users and small businesses. An attacker could leverage the vulnerability to intercept and access sensitive communications between the router and the devices connecting to it.

Tom works for a reputable financial institution. He has a long, complex password that would be near-impossible to guess. He’s memorized it by heart, so he started using it for his social media...

Security flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS. A set of eight separate issues, seven of them with identifiers CVE-2023-47610 through CVE-2023-47616 and another that has yet to be registered, were disclosed last November by security researchers at Kaspersky's ICS CERT division. On Saturday, at the OffensiveCon conference in Berlin, Alexander Kozlov and Sergey Anufrienko will be providing low level technical details about the security issues and how a threat actor could exploit them to take control of vulnerable Telit Cinterion devices.
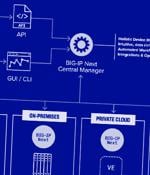
Two security vulnerabilities have been discovered in F5 Next Central Manager that could be exploited by a threat actor to seize control of the devices and create hidden rogue administrator...

F5 has fixed two high-severity BIG-IP Next Central Manager vulnerabilities, which can be exploited to gain admin control and create hidden rogue accounts on any managed assets.Next Central Manager allows administrators to control on-premises or cloud BIG-IP Next instances and services via a unified management user interface.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

CISA warned today that attackers are actively exploiting a maximum-severity GitLab vulnerability that allows them to take over accounts via password resets. The CVE-2023-7028 bug impacts GitLab Community and Enterprise editions, and GitLab fixed it in 16.7.2, 16.5.6, and 16.6.4 and backported patches to versions 16.1.6, 16.2.9, and 16.3.7.

Multiple critical security flaws have been disclosed in the Judge0 open-source online code execution system that could be exploited to obtain code execution on the target system. The three flaws,...

Security researchers have uncovered a "credible" takeover attempt targeting the OpenJS Foundation in a manner that evokes similarities to the recently uncovered incident aimed at the open-source...