Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
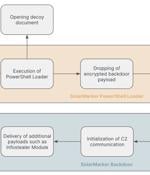
The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from...

While the results of law enforcement action against ransomware-as-a-service operators Alphv/BlackCat and LockBit are yet to be fully realized, the August 2023 disruption of the Qakbot botnet has had one notable effect: ransomware affiliates have switched to vulnerability exploitation as the primary method of delivering the malware. The researchers pointed out other current trends related to ransomware attacks: the attackers' use of vulnerable drivers, legitimate remote desktop tools, custom data exfiltration tools, and abuse of built-in Windows utilities to steal credentials.
The threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure, days after an international law enforcement exercise seized control of its...

LockBit ransomware developers were secretly building a new version of their file encrypting malware, dubbed LockBit-NG-Dev - likely to become LockBit 4.0, when law enforcement took down the cybercriminal's infrastructure earlier this week. While previous LockBit malware is built in C/C++, the latest sample is a work-in-progress written in.

In the wake of yesterday's surprise law enforcement takeover of LockBit's leak site, the UK National Crime Agency and Europol have shared more information about the extent of the takedown. "Today, after infiltrating the group's network, the NCA has taken control of the infrastructure that allows the Lockbit service to operate, compromising their entire criminal enterprise and damaging their credibility," the Agency said.

The threat actors behind the KV-botnet made "behavioral changes" to the malicious network as U.S. law enforcement began issuing commands to neutralize the activity. KV-botnet is the name given to...

Chinese Volt Typhoon state hackers failed to revive a botnet recently taken down by the FBI, which was previously used in attacks targeting critical infrastructure across the United States. After obtaining a court order authorizing it to dismantle the botnet on December 6, FBI agents took control of one of its command-and-control servers and cut off the Chinese hackers' access to the infected devices.

Appliances giant Haier issued a takedown notice to a software developer for creating Home Assistant integration plugins for the company's home appliances and releasing them on GitHub. Haier is a multinational home appliances and consumer electronics corporation selling a wide range of products under the brands General Electric Appliances, Hotpoint, Hoover, Fisher & Paykel, and Candy.

The ransomware group, which has distributed ransomware to more than 1,000 victims, reportedly recovered control of its website on Tuesday. On Dec. 19, the Department of Justice announced the FBI had been working on a disruption campaign against the ransomware group known as ALPHV, Noberus or BlackCat that resulted in the seizure of several of the group's websites, visibility into their network and a decryption tool that could restore stolen data.