Security News
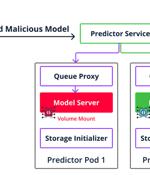
Cybersecurity researchers are warning about the security risks in the machine learning (ML) software supply chain following the discovery of more than 20 vulnerabilities that could be exploited to...

With the increasing reliance on complex and global supply chains, more companies are exposed to a wide range of risks, including theft, counterfeiting, cyberattacks, natural disasters, geopolitical conflicts, and regulatory changes. This customizable policy, written by Franklin Okeke for TechRepublic Premium, outlines the necessary measures and standards that will enhance the resilience of a supply chain.

Threat actors have been observed publishing a new wave of malicious packages to the NuGet package manager as part of an ongoing campaign that began in August 2023, while also adding a new layer of stealth to evade detection. The fresh packages, about 60 in number and spanning 290 versions, demonstrate a refined approach from the previous set that came to light in October 2023, software supply chain security firm ReversingLabs said.
The security team says they found vulnerable CocoaPods pods in "The documentation or terms of service documents of applications provided by Meta, Apple, and Microsoft; as well as in TikTok, Snapchat, Amazon, LinkedIn, Netflix, Okta, Yahoo, Zynga, and many more." E.V.A. reported the vulnerability to CocoaPods in October 2023, at which point it was patched.

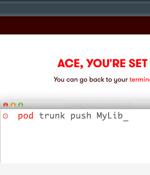
EVA claims CocoaPods in 2014 migrated all "Pods" - a file describing a project's dependencies - to a new "Trunk server" on GitHub. CocoaPods authenticates new devices using an email sent to users who request a session, the researchers noted - but authentication doesn't rely on anything but a client verifying their email address by clicking a link.

A trio of security flaws has been uncovered in the CocoaPods dependency manager for Swift and Objective-C Cocoa projects that could be exploited to stage software supply chain attacks, putting...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The heightened regulatory and legal pressure on software-producing organizations to secure their supply chains and ensure the integrity of their software should come as no surprise. In the last...

Google has taken steps to block ads for e-commerce sites that use the Polyfill.io service after a Chinese company acquired the domain and modified the JavaScript library ("polyfill.js") to...