Security News

The software industry does not currently track the source of all code, nor does it grade the level of security standards applied in these international code factories. Establish a grading scale to rate each piece of code to more effectively determine the risk a company is inheriting from the code.

64% of survey respondents reported that their companies have concerns about security risks for supply chains. Toss in the COVID-19 pandemic and supply chain disruptions, and it's no wonder that enterprises are shifting their cybersecurity strategies.

As the 2021 holiday season approaches, supply chain and logistics, e-commerce and retail, and the travel industry see predictable increases in consumer and business activity - making them more vulnerable to cyber threats and leaving business, employee and consumer data at risk. In addition to increased consumer spending, the 2021 holiday season sees a significant impact on industries coping with the increase in consumer demands.

Imperva's 12-month analysis on cybersecurity risks in the retail industry suggests that the 2021 holiday shopping season will be further disrupted by cybercriminals looking to create chaos and take advantage of an unprecedented global supply chain crisis. Given the widespread impact of the global supply chain crisis, the impact of a single cyber-attack on a retailer in Q4 could be devastating.

Cambridge University researchers have detailed a new way targeted vulnerabilities can be introduced into source code while making them invisible to human code reviewers, allowing for extensive supply-chain attacks. "We have discovered ways of manipulating the encoding of source code files so that human viewers and compilers see different logic. One particularly pernicious method uses Unicode directionality override characters to display code as an anagram of its true logic," professor Ross Anderson explained.

Nobelium has been attempting to replicate the approach it has used in past attacks by targeting organizations integral to the global IT supply chain. This time, it is attacking a different part of the supply chain: resellers and other technology service providers that customize, deploy and manage cloud services and other technologies on behalf of their customers.

The cybercrime group behind the SolarWinds hack remains focused on the global IT supply chain, says Microsoft, with 140 resellers and service providers targeted since May. The Russian-backed hacking group responsible for the SolarWinds attack has been targeting more companies with the goal of disrupting the worldwide IT supply chain.In a blog post published Monday, Microsoft cautioned of new attacks by Nobelium, revealing that it notified 140 resellers and technology service providers targeted by the group.

Lazarus Group, the advanced persistent threat group attributed to the North Korean government, has been observed waging two separate supply chain attack campaigns as a means to gain a foothold into corporate networks and target a wide range of downstream entities. The latest intelligence-gathering operation involved the use of MATA malware framework as well as backdoors dubbed BLINDINGCAN and COPPERHEDGE to attack the defense industry, an IT asset monitoring solution vendor based in Latvia, and a think tank located in South Korea, according to a new Q3 2021 APT Trends report published by Kaspersky.
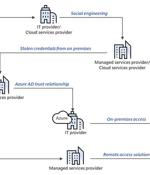
Nobelium, the threat actor behind the SolarWinds compromise in December 2020, has been behind a new wave of attacks that compromised 14 downstream customers of multiple cloud service providers, managed service providers, and other IT services organizations, illustrating the adversary's continuing interest in targeting the supply chain via the "Compromise-one-to-compromise-many" approach. Microsoft, which disclosed details of the campaign on Monday, said it notified more than 140 resellers and technology service providers since May. Between July 1 and October 19, 2021, Nobelium is said to have singled out 609 customers, who were collectively attacked a grand total of 22,868 times.

Lazarus - a North Korean advanced persistent threat group - is working on launching cyberespionage-focused attacks on supply chains with its multi-platform MATA framework. The MATA malware framework can target three operating systems: Windows, Linux and macOS. MATA has historically been used to steal customer databases and to spread ransomware in various industries, but in June, Kaspersky researchers tracked Lazarus using MATA for cyber-espionage.