Security News

Researchers from the National University of Singapore and Yonsei University in South Korea have devised a mobile application that uses smartphones' time-of-flight sensor to find tiny spy cameras hidden in everyday objects. The app is more successful at detecting hidden cams than existing state-of-the-art commercial hidden camera detectors and much more successful than the human eye/brain.

Recent model smartphones can be smarter still about finding hidden cameras in their vicinity, if they take advantage of time-of-flight sensors. Sriram Sami, Bangjie Sun, and Sean Rui Xiang Tan, from National University of Singapore, and Jun Han from Yonsei University, describe how this might be done in a paper [PDF] titled "LAPD: Hidden Spy Camera Detection using Smartphone Time-of-Flight Sensors".

The Office of the Commissioner for Personal Data Protection in Cyprus has collected a $1 million fine from intelligence company WiSpear for gathering mobile data from various individuals arriving at the airport in Larnaca. While this is just an administrative fine under the European Union's General Data Protection Regulation, it is related to a scandal two years ago widely publicized as the "Spy van" case.

Although the accommodation booking website reportedly asked the Dutch AIVD spy agency for help with the breach after its internal investigation identified "Andrew" as having connections to US spy agencies, it did not notify either its affected customers or data protection authorities in the Netherlands at the time, the newspaper allged. "When we asked for comment about the allegations, a Booking.com spokesperson told us:"With the support of external subject matter experts and following the framework established by the Dutch Data Protection Act, we confirmed that no sensitive or financial information was accessed.

The US Federal Communications Commission has terminated China Telecom's authority to provide communications services in the USA. In its announcement of the termination, the government agency explained the decision is necessary because the national security environment has changed in the years since 2002. That was when China Telecom was first allowed to operate in the USA. The FCC now believes - partly based on classified advice from national security agencies - that China Telecom can "Access, store, disrupt, and/or misroute U.S. communications, which in turn allow them to engage in espionage and other harmful activities against the United States".

The threat actor's goal is Microsoft Office 365 account takeovers. Microsoft, which began tracking the activity in late July 2021, detailed the attacks in an alert released Monday, adding that the culprits appear to be bent on espionage and have ties to Iran.

NSO Group's Pegasus malware was used to spy on Dubai princess's lawyers during child custody dispute
Cherie Blair tipped off a Jordanian princess that the royal's estranged husband, the Sheikh of Dubai, had deployed NSO Group's Pegasus malware against her and her lawyers, a series of explosive High Court judgments [PDFs] have revealed. Sheikh Mohammed bin Rashid al Maktoum, the absolute ruler of Dubai, was found to have ordered the deployment of one of the world's most potent malware strains against Princess Haya bint Hussein, his former wife and a member of the Jordanian royal family, during a bitter court battle over custody of their children.
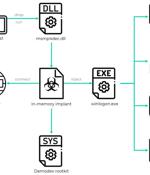
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems. Attacks mounted by the hacking group, dubbed GhostEmperor by Kaspersky, are also said to have used a "Sophisticated multi-stage malware framework" that allows for providing persistence and remote control over the targeted hosts.

A cyberespionage group dubbed "FamousSparrow" by researchers has taken flight, targeting hotels, governments and private organizations around the world with a custom backdoor called, appropriately, "SparrowDoor." It's one of the advanced persistent threats that targeted the ProxyLogon vulnerabilities earlier this year, according to ESET, though its activity has only recently come to light. According to the firm, the backdoor's malicious actions include the ability to: rename or delete files; create directories; shut down processes; send information such as file attributes, file size and file write time; exfiltrate the content of a specified file; write data to a specified file; or establish an interactive reverse shell.

The novel backdoor technique called SideWalk, seen in campaigns targeting US media and retailers late last month, has been tied to an adversary that's been around for quite a while: namely, China-linked Grayfly espionage group. According to a report published by Symantec on Thursday, the SideWalk malware has been deployed in recent Grayfly campaigns against organizations in Taiwan, Vietnam, the US and Mexico.