Security News
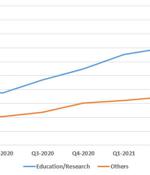
Facilities in the sector saw an average of 1,739 attacks per organization each week last month, according to Check Point Research. A report published Wednesday by cyber threat intelligence provider Check Point Research looks at the latest wave of cyberattacks against educational and research facilities in particular and offers tips on how to better combat them.

In his new role as the Head of Research and Intelligence at Cyble, Kaustubh will be driving the research initiatives of Cyble and overseeing and operationalize the development of the company's security research and client delivery initiatives. He will play a pivotal role in leading Cyble's threat intelligence capabilities to foster the production of strategic and actionable threat research and accelerate the integration of Cyble's services across the world.

"To some extent, this data supports the theory that the cybersecurity skills shortage is related to mismanagement rather than a dearth of qualified candidates or advanced skills." The skills gap is partly a self-inflicted wound on the industry by the industry.

Attack protection specialist Cybereason has fingered threat actors working on behalf of "Chinese state interests" as being behind attacks on telcos operating in Southeast Asia - with some having been prowling the penetrated networks for information on high-value targets since 2017. "Telcos are a prime target for nation-state espionage programs for various reasons, among them, the ability to collect information about the telco's subscribers," Assaf Dahan, senior director and head of threat research at Cybereason, told.

That's why I believe the first step to bringing more women into the field of cybersecurity - and the greatest catalyst to their success in the industry - is female inspiration and mentorship. Today, many women base their decisions to join a company on whether there are other women working there, especially in positions of leadership.

A group of academic researchers has created a tool that can be used to clone Android malware and test the resilience of these new variants against anti-malware detection. Testing against 17 commercial anti-malware engines has shown that half don't detect the clones.

The South Korean Atomic Energy Research Institute has confirmed that an unknown third-party gained unauthorized access to its systems. "Currently, the Atomic Energy Research Institute is investigating the subject of the hacking and the amount of damage," the institute also said.

South Korean officials have admitted that government nuclear think tank Korea Atomic Energy Research Institute was hacked in May 2021 by North Korea's Kimsuky group. Malware analyst group IssueMakersLab said in a report that it detected an attack on KAERI on May 14th. The attack saw incoming heat from 13 internet addresses, of which one was traceable to Kimsuky.

South Korea's state-run Korea Atomic Energy Research Institute on Friday disclosed that its internal network was infiltrated by suspected attackers operating out of its northern counterpart. KAERI, established in 1959 and situated in the city of Daejeon, is a government-funded research institute that designs and develops nuclear technologies related to reactors, fuel rods, radiation fusion, and nuclear safety.

South Korea's 'Korea Atomic Energy Research Institute' disclosed yesterday that their internal networks were hacked last month by North Korean threat actors using a VPN vulnerability. The Korea Atomic Energy Research Institute, or KAERI, is the governement-sponsored institute for the research and application of nuclear power in South Korea.