Security News

Intel's issue reflects a wider concern: Legacy technology can introduce cybersecurity weaknesses. This creates a long tail of old products that remain in widespread use, vulnerable to attacks.

Bugcrowd released a report which provides CIOs and CISOs valuable insight on ethical hackers and the economics of security research. This comprehensive annual study offers an in-depth look at ethical hackers to reveal how they reduce risk, which industries leverage their expertise most, and what organizations are doing to attract high-performing security researchers to their programs.

64% of survey respondents reported that their companies have concerns about security risks for supply chains. Toss in the COVID-19 pandemic and supply chain disruptions, and it's no wonder that enterprises are shifting their cybersecurity strategies.

Increasing numbers of "Non-business" Internet of Things devices are showing up inside corporate networks, Palo Alto Networks has warned, saying that smart lightbulbs and internet-connected pet feeders may not feature in organisations' threat models. According to Greg Day, VP and CSO EMEA of the US-based enterprise networking firm: "When you consider that the security controls in consumer IoT devices are minimal, so as not to increase the price, the lack of visibility coupled with increased remote working could lead to serious cybersecurity incidents."

All those dubious excuses needed by traditional romance scammers to talk you into using wire transfer services to send money, or into buying them gift cards and sending through the redemption codes, are replaced by a sense of structure: there's a genuine app for this investment! The cryptorom scammers will even offer you an app if you have an iPhone, where Apple's "Walled garden" approach of requiring all consumer app downloads to come from the Apple App Store almost certainly persuades many victims that the cryptorom app must indeed have some sort of official authorisation or approval.

There's a fine line between getting hold of data that may be in the public interest and downright stealing data just because you can. To kick off, Marcello Ienca, a research fellow at the Swiss Federal Institute of Technology, and Effy Vayena, deputy head of the Swiss Institute of Translational Medicine, offered the definition that "Hacked" data is "Data obtained in an unauthorized manner through illicit access to a computer or computer network." They claim it is increasingly being used in scientific research such as conflict modelling studies based on WikiLeaks datasets, and studies on sexual behaviour based on data leaked from Ashley Madison, a dating website whose database was pilfered by a group of attackers calling themselves The Impact Team in 2015.

Openc8... is applicable to a range of iPhone models all the way up to the iPhone X - though the research paper focuses on its use in the iTimed toolkit to audit and attack the Apple A10 Fusion chip inside an iPhone 7. The trio's - Seetal Potluri was the third researcher - checkm8 reimplementation, which brings with it a range of claimed improvements, is dubbed openc8, and is applicable to a range of iPhone models all the way up to the iPhone X - though the research paper focuses on its use in the iTimed toolkit to audit and attack the Apple A10 Fusion chip inside an iPhone 7.

Infosec firm Rapid7 has joined the chorus of voices urging reform to the UK's Computer Misuse Act, publishing its detailed proposals intended to change the cobwebby old law for the better. "It's worth noting that neither the National Crime Agency or the CPS seem to be recklessly pursuing frivolous investigations or prosecutions of good-faith security research. Nonetheless, the current legal language does expose researchers to legal risk and uncertainty, and it would be good to see some clarity on the topic," said Rapid7 in a blog post published over the sleepy summer period.
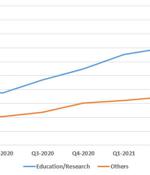
Facilities in the sector saw an average of 1,739 attacks per organization each week last month, according to Check Point Research. A report published Wednesday by cyber threat intelligence provider Check Point Research looks at the latest wave of cyberattacks against educational and research facilities in particular and offers tips on how to better combat them.

In his new role as the Head of Research and Intelligence at Cyble, Kaustubh will be driving the research initiatives of Cyble and overseeing and operationalize the development of the company's security research and client delivery initiatives. He will play a pivotal role in leading Cyble's threat intelligence capabilities to foster the production of strategic and actionable threat research and accelerate the integration of Cyble's services across the world.