Security News

One in every six ransomware attacks targeting US government offices was traced back to the LockBit ransomware group, according to Trend Micro. Overall ransomware attack victim numbers increased by 47% from H2 2022.

Johnson Controls International has suffered what is described as a massive ransomware attack that encrypted many of the company devices, including VMware ESXi servers, impacting the company's and its subsidiaries' operations.Yesterday, a source told BleepingComputer that Johnson Controls suffered a ransomware attack after initially being breached at its Asia offices.

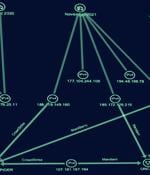
Cybersecurity experts have shed light on a new cybercrime group known as ShadowSyndicate (formerly Infra Storm) that may have leveraged as many as seven different ransomware families over the past...

Group-IB analysts attribute with various degrees of confidence ShadowSyndicate's use of the Quantum, Nokoyawa, BlackCat/ALPHV, Clop, Royal, Cactus, and Play ransomware in breaches since July 2022. Based on their findings, researchers believe that the threat actor could be an initial access broker, although evidence suggests that ShadowSyndicate is an affiliate to multiple ransomware operations.

Despite some positive developments, the impact of ransomware attacks remains high, according to SpyCloud. Infostealer infections preceded 22% of ransomware events for North American and European ransomware victim companies in 2023 - with common infostealers such as Raccoon, Vidar, and Redline increasing the probability even further.

The City of Dallas, Texas, said this week that the Royal ransomware attack that forced it to shut down all IT systems in May started with a stolen account. Royal gained access to the City's network using a stolen domain service account in early April and maintained access to the compromised systems between April 7 and May 4.

Overall cyber insurance claims frequency increased by 12% in the first half of 2023, according to Coalition. Companies with over $100 million in revenue saw the largest increase in the number of claims as well as more substantial losses from attacks - with a 72% increase in claims severity from 2H 2022.
A financially motivated threat actor has been outed as an initial access broker (IAB) that sells access to compromised organizations for other adversaries to conduct follow-on attacks such as...

The Snatch ransomware crew has listed on its dark-web site the Florida Department of Veterans' Affairs as one of its latest victims - as the Feds warn organizations to be on the lookout for indicators of compromise linked to the extortionist gang. "After data exfiltration often involving direct communications with victims demanding ransom, Snatch threat actors may threaten victims with double extortion, where the victims' data will be posted on Snatch's extortion blog if the ransom goes unpaid," according to a joint advisory issued by the FBI and the US Cybersecurity and Infrastructure Security Agency on Wednesday.

The financially motivated threat actor known as UNC3944 is pivoting to ransomware deployment as part of an expansion to its monetization strategies, Mandiant has revealed. "UNC3944 has demonstrated a stronger focus on stealing large amounts of sensitive data for extortion purposes and they appear to understand Western business practices, possibly due to the geographical composition of the group," the threat intelligence firm said.