Security News

The US National Institute of Standards and Technology has recommended four cryptographic algorithms for standardization to ensure data can be protected as quantum computers become more capable of decryption. Back in 2015, the NSA announced plans to transition to quantum-resistant cryptographic algorithms in preparation for the time when quantum computers make it possible to access data encrypted by current algorithms, such as AES and RSA. No one is quite sure when that may occur but it depends on the number of qubits - quantum bits - that a quantum machine can muster, and other factors, such as error correction.
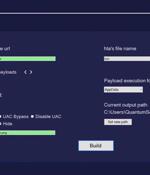
A new malware tool that enables cybercriminal actors to build malicious Windows shortcut files has been spotted for sale on cybercrime forums. Dubbed Quantum Lnk Builder, the software makes it possible to spoof any extension and choose from over 300 icons, not to mention support UAC and Windows SmartScreen bypass as well as "Multiple payloads per.LNK" file.

LNKs are Windows shortcut files that can contain malicious code to abuse legitimate tools on the system, the so-called living-off-the-land binaries, such as PowerShell or the MSHTA that is used to execute Microsoft HTML Application files. Researchers at Cyble have spotted a new tool for creating malicious LNKs called Quantum, which features a graphical interface and offers convenient file building through a rich set of options and parameters.

It's unclear when quantum computers will easily crack classical crypto - estimates range from three to five years to never - but conventional wisdom is that now's the time to start preparing to ensure data remains encrypted. QuSecure, which is launching this week after three years in stealth mode, will offer a fully managed service approach with QuProtect, which is designed to not only secure data now against conventional threats but also against future attacks from nation-states and bad actors leveraging quantum systems.

The NSA already has classified quantum-resistant algorithms of its own that it developed over many years, said Joyce. The agency's mathematicians worked with NIST to support the process, trying to crack the algorithms in order to test their merit.

President Joe Biden signed a national security memorandum on Thursday asking government agencies to implement measures that would mitigate risks posed by quantum computers to US national cyber security. The multi-year effort to migrate all vulnerable cryptographic systems to quantum-resistant cryptography will span over 50 government departments and agencies that use National Security Systems.

US president Joe Biden issued two directives on Wednesday aimed at ensuring the nation - and like-minded friends - remain ahead of other countries in the field of quantum computing. The committee is an enhancement to the National Quantum Initiative Act - a 2018 law that provides $1.2 billion and a plan for advancing quantum tech.

Nimbuspwn bugs allow attackers to gain root privileges on some Linux machinesMicrosoft has unearthed two security vulnerabilities in the networkd-dispatcher daemon that may be exploited by attackers to gain root on many Linux endpoints, allowing them to deploy backdoors, malware, ransomware, or perform other malicious actions. The 15 most exploited vulnerabilities in 2021In 2021, threat actors aggressively exploited newly disclosed critical software vulnerabilities to hit a broad set of targets worldwide, says the latest advisory published by the US Cybersecurity and Infrastructure Security Agency.

A group wielding the Quantum Locker ransomware is hitting targets in a blitzkrieg-like manner, going from intial compromise to domain-wide deployment and execution in under four hours, researchers with The DFIR Report are warning. The threat of ransomware continues unabated and attackers are becoming increasingly adept at executing attacks speedily, giving defenders only a small window of opportunity to detect, respond to and mitigate them.

The Quantum ransomware, a strain first discovered in August 2021, were seen carrying out speedy attacks that escalate quickly, leaving defenders little time to react. The technical details of a Quantum ransomware attack were analyzed by security researchers at The DFIR Report, who says the attack lasted only 3 hours and 44 minutes from initial infection to the completion of encrypting devices.