Security News

A huge phishing campaign exploited a security blind-spot in Proofpoint's email filtering systems to send an average of three million "Perfectly spoofed" messages a day purporting to be from Disney, IBM, Nike, Best Buy, and Coca-Cola - all of which are Proofpoint customers. Guardio dubbed the campaign EchoSpoofing - because the spam was "Echoed" from email relay servers owned and operated by Proofpoint itself.

A massive phishing campaign dubbed "EchoSpoofing" exploited now-fixed, weak permissions in Proofpoint's email protection service to dispatch millions of spoofed emails impersonating big entities like Disney, Nike, IBM, and Coca-Cola, to target Fortune 100 companies. The campaign started in January 2024, disseminating an average of 3 million spoofed emails daily and reaching a peak of 14 million emails in early June.
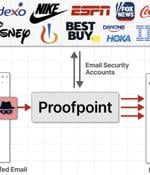
An unknown threat actor has been linked to a massive scam campaign that exploited an email routing misconfiguration in email security vendor Proofpoint's defenses to send millions of messages spoofing various popular companies like Best Buy, IBM, Nike, and Walt Disney, among others. "These emails echoed from official Proofpoint email relays with authenticated SPF and DKIM signatures, thus bypassing major security protections - all to deceive recipients and steal funds and credit card details," Guardio Labs researcher Nati Tal said in a detailed report shared with The Hacker News.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

In Proofpoint's 2024 Voice of the CISO report, the cybersecurity company found that CISOs are dealing with people-centric threats more than ever. According to the survey, more CISOs than ever believe human error is the biggest vulnerability for their organizations; 74% of the CISOs feel this way, up from 60% in 2023.

Cyber security company Proofpoint recently surveyed 7,500 employees and 1,050 security professionals in 15 countries, including Australia, Japan, South Korea and Singapore. Employees in the Asia-Pacific region were the most likely among global employees surveyed to say they were unsure about their personal responsibility for cyber security.

Recruiters and anyone else involved in hiring processes should be knowledgeable about this social engineering attack threat. A new report from U.S.-based cybersecurity company Proofpoint exposes a new attack campaign operated by a financially-oriented threat actor dubbed TA4557 with high financial data theft risks and possibly more risks such as intellectual property theft.

Syncro has launched a new agreement with Proofpoint to enable Syncro's MSP partners to offer their customers access to Proofpoint's email security and security awareness training solutions. "This reseller agreement not only allows our MSPs to give their customers superior security in a world where safeguarding users is critical, it also provides an opportunity to increase revenue with existing and prospective customers," said Emily Glass, CEO at Syncro.

"Despite defenders' best efforts, cybercriminals continue to defraud, extort, and ransom companies for billions of dollars annually," said Sherrod DeGrippo, vice president of threat research and detection at Proofpoint. Proofpoint entered into the report with a number of assumptions in place, detailing what methods threat actors would go to to carry out an attack, as well as the methods employed to help carry out such attacks.

Then we had two-factor authentication - and now Proofpoint reckons criminals online are able to start bypassing them with transparent reverse proxies. In a blog post Proofpoint said it sees "Numerous MFA phishing kits ranging from simple open-source kits with human readable code and no-frills functionality to sophisticated kits utilizing numerous layers of obfuscation and built-in modules that allow for stealing usernames, passwords, MFA tokens, social security numbers and credit card numbers."