Security News

An app with the name Signal Plus Messenger was available on Play for nine months and had been downloaded from Play roughly 100 times before Google took it down last April after being tipped off by security firm ESET. It was also available in the Samsung app store and on signalplus[. An app calling itself FlyGram was created by the same threat actor and was available through the same three channels.

The Google Cloud security team acknowledged a common tactic known as versioning used by malicious actors to slip malware on Android devices after evading the Google Play Store's review process and...

Threat actors are leveraging a technique called versioning to evade Google Play Store's malware detections and target Android users. Earlier this May, ESET discovered a screen recording app named "iRecorder - Screen Recorder" that remained innocuous for nearly a year after it was first uploaded to the Play Store before malicious changes were introduced sneakily to spy on its users.

A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000 downloads in total since 2022. Kaspersky, which identified 11 apps on the official app storefront, said the malware masqueraded as legitimate photo editing apps, camera, and smartphone wallpaper packs.

A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than 60 legitimate apps that collectively have over 100 million downloads. An additional eight million installations have been tracked through ONE store, a leading third-party app storefront in South Korea.

If you want to sneak malware onto people's Android devices via the official Google Play store, it may cost you about $20,000 to do so, Kaspersky suggests. Before cybercriminals can share their malicious apps from Google's official store, they'll need a Play developer account, and Kaspersky says those sell for between $60 and $200 each.
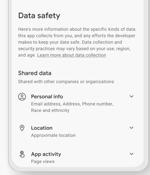
An investigation into data safety labels for Android apps available on the Google Play Store has uncovered "Serious loopholes" that allow apps to provide misleading or outright false information. The study, conducted by the Mozilla Foundation as part of its *Privacy Not Included initiative, compared the privacy policies and labels of the 20 most popular paid apps and the 20 most popular free apps on the app marketplace.

Google has removed two new malicious dropper apps that have been detected on the Play Store for Android, one of which posed as a lifestyle app and was caught distributing the Xenomorph banking malware. "Xenomorph is a trojan that steals credentials from banking applications on users' devices," Zscaler ThreatLabz researchers Himanshu Sharma and Viral Gandhi said in an analysis published Thursday.

In brief A quartet of malware-laden Android apps from a single developer have been caught with malicious code more than once, yet the infected apps remain on Google Play and have collectively been downloaded more than one million times. Google Play has a history of hosting malicious apps, with perhaps one of the most egregious cases coming to light this past July when 60 apps installed by more than 3.3 million users were taken down due to malware.
A set of four Android apps released by the same developer has been discovered directing victims to malicious websites as part of an adware and information-stealing campaign. The apps, published by a developer named Mobile apps Group and currently available on the Play Store, have been collectively downloaded over one million times.