Security News

Phishing PyPI users: Attackers compromise legitimate projects to push malwarePyPI, the official third-party software repository for Python packages, is warning about a phishing campaign targeting its users. DDoS tales from the SOCIn this Help Net Security video, Bryant Rump, Principal Security Architect at Neustar Security Services, talks about the challenges of mitigating immense DDoS attacks.

The community-run organization said this is the first known phishing attack against PyPI users. "The phishing message claims that there is a mandatory 'validation' process being implemented, and invites users to follow a link to validate a package, or otherwise risk the package being removed from PyPI," the organization said via Twitter, adding that it never removes valid projects from the registry, only those violating terms of service.

DoorDash has confirmed that "a small percentage" of its customers' data and employees' information, including names, email and delivery addresses, phone numbers, and order and partial credit card details, were revealed as part of a broad phishing campaign dubbed Oktapus. "We can confirm the incident is connected to a wider, sophisticated phishing campaign that has targeted several other companies," a company spokesperson told The Register.

Criminals behind the cyberattack attempts on Twilio and Cloudflare earlier this month had cast a much wider net in their phishing expedition, targeting as many as 135 organizations - primarily IT, software development and cloud services providers based in the US. The gang went after the employees of Okta customers, sending victims text messages with malicious links to sites spoofing their company's authentication page to harvest their work login credentials and multi-factor authentication codes. In research published Thursday, the threat intel team revealed the Oktapus phishing trip, which began in March, snaffled 9,931 user credentials and 5,441 multi-factor authentication codes.

Hackers responsible for a string of recent cyberattacks, including those on Twilio, MailChimp, Cloudflare, and Klaviyo, compromised over 130 organizations in the same phishing campaign. This phishing campaign utilized a phishing kit codenamed '0ktapus' to steal 9,931 login credentials that the hackers then used to gain access to corporate networks and systems through VPNs and other remote access devices.

Microsoft observed a campaign that inserted an attacker-controlled proxy site between the account users and the work server they attempted to log into. When the user entered a password into the proxy site, the proxy site sent it to the real server and then relayed the real server's response back to the user.

A phishing campaign caught yesterday was seen targeting maintainers of Python packages published to the PyPI registry. Python packages 'exotel' and 'spam' are among hundreds seen laced with malware after attackers successfully compromised accounts of maintainers who fell for the phishing email.

PyPI, the official third-party software repository for Python packages, is warning about a phishing campaign targeting its users. "We have additionally determined that some maintainers of legitimate projects have been compromised, and malware published as the latest release for those projects. These releases have been removed from PyPI and the maintainer accounts have been temporarily frozen," the PyPI team noted.
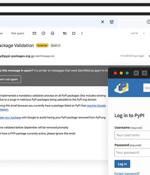
The Python Package Index, PyPI, on Wednesday sounded the alarm about an ongoing phishing campaign that aims to steal developer credentials and inject malicious updates to legitimate packages. "This is the first known phishing attack against PyPI," the maintainers of the official third-party software repository said in a series of tweets.

Threat actors are increasingly abusing legitimate software-as-a-service platforms like website builders and personal branding spaces to create malicious phishing websites that steal login credentials. Because SaaS platforms simplify and streamline the process of creating new sites, phishing actors can easily switch to different themes, scale up or diversify their operations, and quickly respond to reports and takedowns.